3,200 Vendor Records Leaked in Airbus Cybersecurity Incident
🚨 Airbus suffers a significant data breach affecting 3,200 vendors. Sensitive supplier information has been leaked, raising cybersecurity concerns in the aerospace sector. Stay informed and secure! #CyberSecurity #DataBreach #Airbus
Company Overview
- Airbus SE: A global leader in the aerospace and defense sectors, headquartered in Leiden, Netherlands, with its operational hub in Toulouse, France. Airbus is renowned for manufacturing commercial aircraft, military hardware, helicopters, and space-related systems. The company works closely with a vast network of vendors and suppliers across the globe.
Breach Details
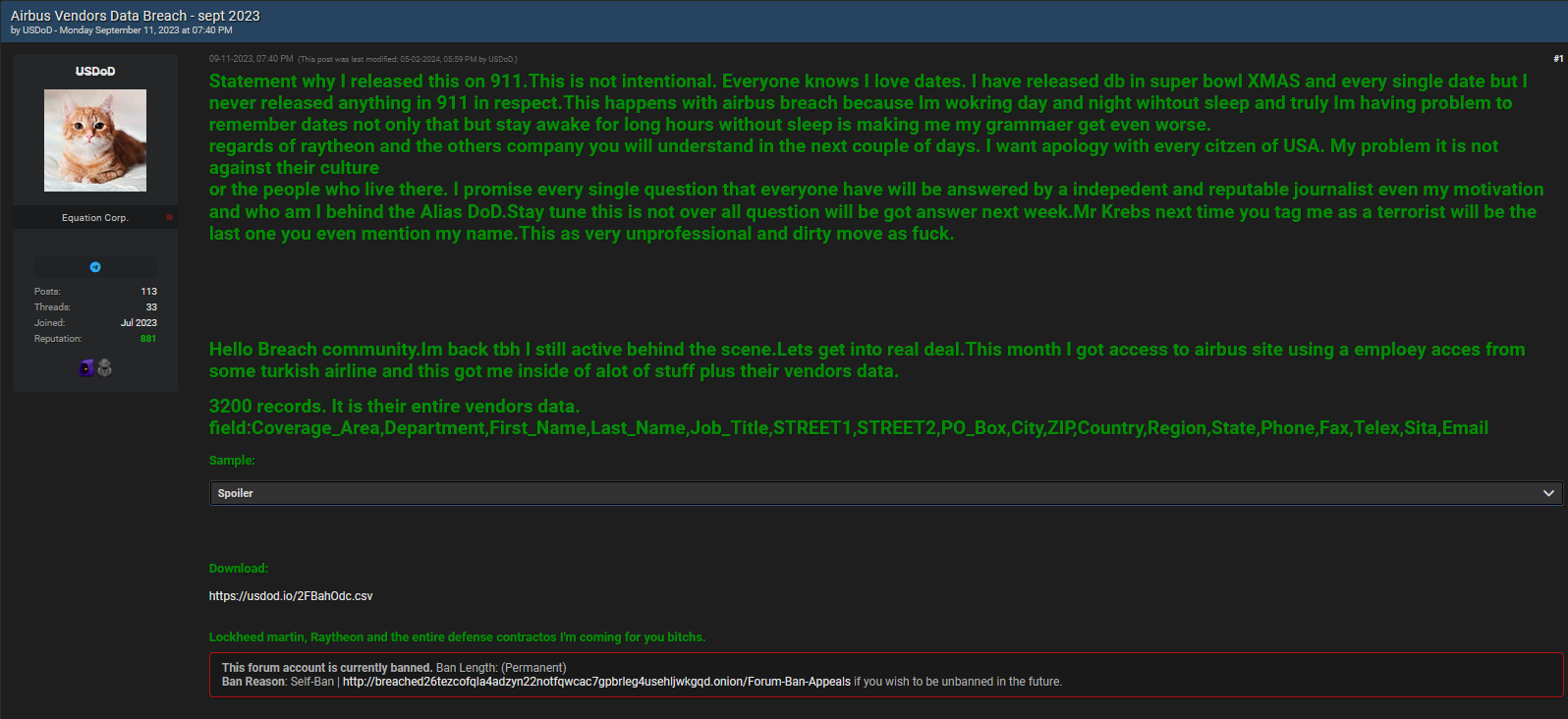
- Date of Incident: September 11, 2023
- Threat Actor: A cybercriminal using the alias "USD0D."
- Incident Description: The hacker gained unauthorized access to Airbus' vendor data through compromised credentials from a Turkish airline employee. The breach resulted from the installation of malware on the employee's system, likely originating from a pirated version of the Microsoft .NET framework. This malware, identified as RedLine, is known for stealing sensitive information.
- Data Exposed: Information from 3,200 Airbus vendors was compromised, including:
- Names, addresses, phone numbers, and email addresses.
- Specific data fields: Coverage Area, Department, Job Titles, and more.
- Leak Method: The attacker posted the data on BreachForums, a notorious dark web forum, without making any ransom demands. This action indicates a motive focused more on causing disruption and harm rather than financial gain(Krebs on Security,Cybersecurity News).
Threat Actor Profile
- Alias: USD0D
- Previous Activity: USD0D is believed to be associated with the "Ransomed" ransomware group and was also involved in the December 2022 FBI InfraGard breach, where sensitive information about 80,000 individuals was exposed.
- Motivation: The hacker has a history of targeting high-profile entities in the defense and aerospace sectors, which suggests motives potentially linked to both financial gain and ideological reasons. The hacker explicitly threatened further attacks on prominent defense contractors like Lockheed Martin and Raytheon(Cybersecurity News,The Record from Recorded Future).
Impact Analysis
- Primary Impact: Exposure of sensitive vendor information increases the risk of targeted phishing campaigns, business email compromise (BEC), and potential account takeovers, which can lead to further breaches within Airbus' supply chain.
- Secondary Impact: The breach could significantly harm Airbus's relationships with its vendors and suppliers, leading to a loss of trust and potential legal and regulatory consequences. European data regulators may scrutinize Airbus’s data protection measures in light of this incident.
- Wider Implications: The aerospace and defense industries are frequently targeted by both financially motivated cybercriminals and state-sponsored actors due to the sensitive nature of the data they hold. This breach highlights ongoing vulnerabilities in the supply chain, especially when third-party partners are involved(CPO Magazine,The Record from Recorded Future).




