Atlassian Jira Zero-Day Vulnerability Exploit For Sale
🛡️ Heads Up: A new zero-day exploit affecting Jira is circulating on the dark web. Learn how to safeguard your systems and data. #InfoSec #DataProtection
Atlassian is a leading software company known for its suite of productivity tools designed for team collaboration and project management. Key products include Jira, Confluence, and Trello, which are widely used across various industries to streamline workflows and enhance team communication.
Breach Details
Incident Date: June 16, 2024
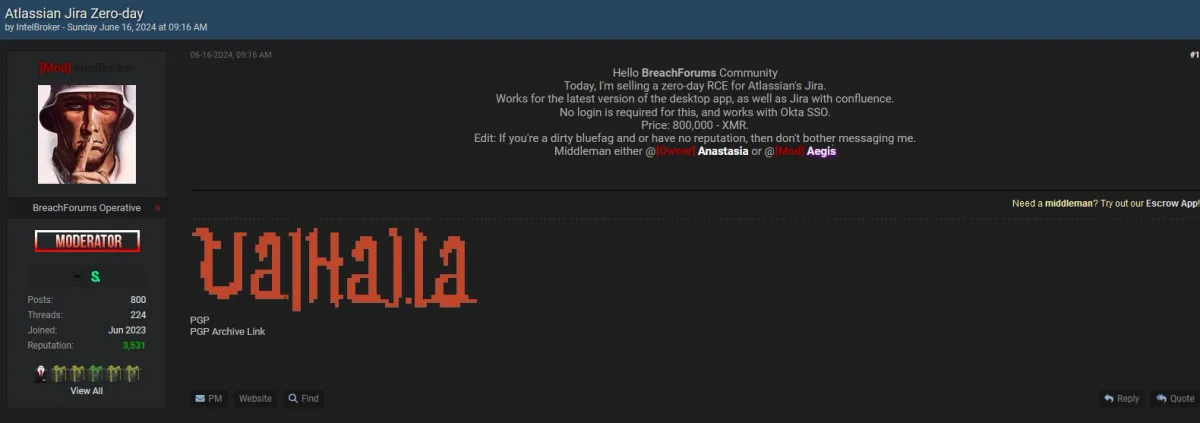
Discovery: A post was discovered on BreachForums, a notorious platform for trading and selling cyber exploits and stolen data. The post, created by a user named IntelBroker, advertises a zero-day Remote Code Execution (RCE) vulnerability affecting Atlassian's Jira software.
Vulnerability Specifics:
- Software Affected: Atlassian Jira (including the latest desktop version and Jira with Confluence integration)
- Authentication Bypass: No login required, compatible with Okta Single Sign-On (SSO)
- Price: 800,000 XMR (Monero cryptocurrency)
- Seller: IntelBroker, a moderator on BreachForums with a reputation score of 3,531
Threat Actor Profile
Username: IntelBroker
- Role: Moderator on BreachForums
- Joined: June 2023
- Reputation: 3,531 (indicative of a well-established presence in the cybercrime community)
Behavior and Tactics:
- Sales Approach: Direct sale of exploit with the option for a middleman to ensure transaction security.
- Exclusivity: Refusal to engage with buyers who lack reputation or trust within the community.
Impact Analysis
Potential Risks:
- Unauthorized Access: Exploitation of the zero-day could allow attackers to gain unauthorized access to Jira instances, potentially compromising sensitive project data and internal communications.
- Data Breach: Organizations using Jira with Confluence integration are particularly at risk, as the exploit could lead to broader data breaches.
- Business Disruption: Exploitation could result in significant operational disruptions, especially for companies heavily reliant on Jira for project management.
Affected Parties:
- Businesses and Enterprises: Particularly those using Jira for critical project management tasks.
- Developers and IT Teams: Need to be on high alert to detect and mitigate any potential exploitation of this vulnerability.
Prevention Tips
- Update and Patch Management:
- Regularly update Atlassian products and apply security patches promptly.
- Monitor Atlassian’s official channels for any emergency patches or updates related to this zero-day vulnerability.
- Enhanced Security Measures:
- Implement multi-factor authentication (MFA) across all systems, including Jira and Confluence.
- Restrict access to sensitive data and project management tools to only those who need it.
- Network and Endpoint Security:
- Use advanced endpoint protection solutions to detect and block exploit attempts.
- Implement network segmentation to limit the spread of any potential breaches.
- User Awareness and Training:
- Educate employees about the risks of phishing and social engineering attacks that could lead to exploit utilization.
- Conduct regular security training sessions to keep staff informed about the latest cybersecurity threats.




