Cas lists: 'New' 0Day Linux LPE, Price: 169K BTC & XMR
Cas lists a new 0day.
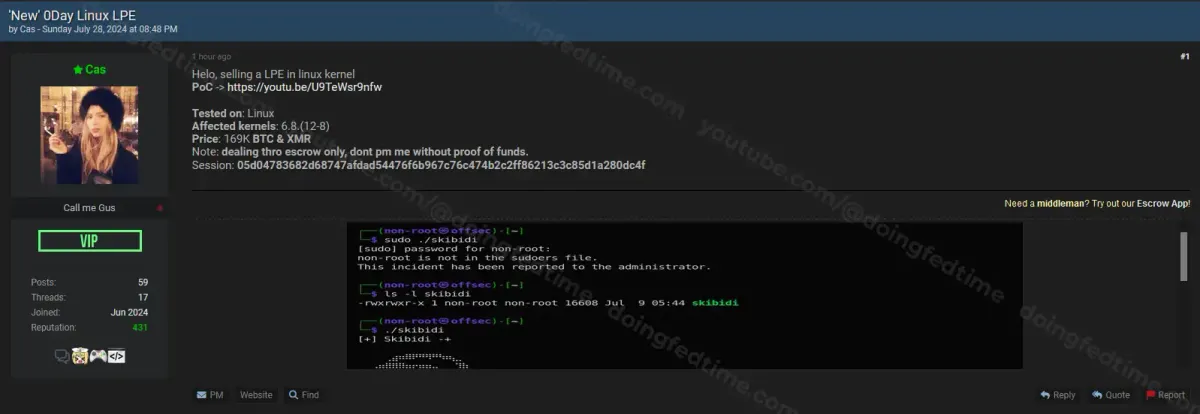
A recent post on a dark web forum is advertising a new Local Privilege Escalation (LPE) exploit for the Linux kernel. This report explains the exploit in simple terms and provides details for better understanding and awareness.
What is an Exploit?
An exploit is a piece of software or code that takes advantage of a vulnerability (weakness) in a computer system. In this case, the exploit targets the Linux operating system, specifically its kernel.
What is a Local Privilege Escalation (LPE)?
Local Privilege Escalation (LPE) is a type of attack where a hacker gains higher access rights (privileges) on a system than they should have. For example, an attacker who has limited user access can use an LPE exploit to gain administrative (root) access, which allows them to control the system completely.
Breach Details
- Exploit Type: Local Privilege Escalation (LPE)
- Affected Systems: Linux kernel versions 6.8 (versions 12-8)
- Asking Price: 169K BTC & XMR (Bitcoin and Monero, cryptocurrencies)
- Proof of Concept (PoC): Available on YouTube (link provided in the post)
- Session ID: 05d04783682d68747afdad54476f6b967c76c474b2c2ff86213c3c85d1a280dc4f
Transaction and Communication
- The seller, using the alias "Cas," insists on using an escrow service for transactions to ensure security and trust. The seller warns against direct messages without proof of funds, indicating a high level of caution.
Understanding the Threat
Potential Risks
- System Control: An attacker using this exploit can gain full control over the affected system, allowing them to steal data, install malware, or perform any action as if they were the system administrator.
- Wide Impact: Since many systems use the affected versions of the Linux kernel, a large number of systems could be vulnerable if the exploit is widely distributed.