Cisco Licensing Utility Under Siege: Backdoor Account Exploited in the Wild
Reports are emerging that malicious actors are actively exploiting a critical vulnerability in unpatched Cisco Smart Licensing Utility (CSLU) instances.
Reports are emerging that malicious actors are actively exploiting a critical vulnerability in unpatched Cisco Smart Licensing Utility (CSLU) instances. The flaw, stemming from a built-in, undocumented administrative account, allows unauthorized access and control of affected systems.
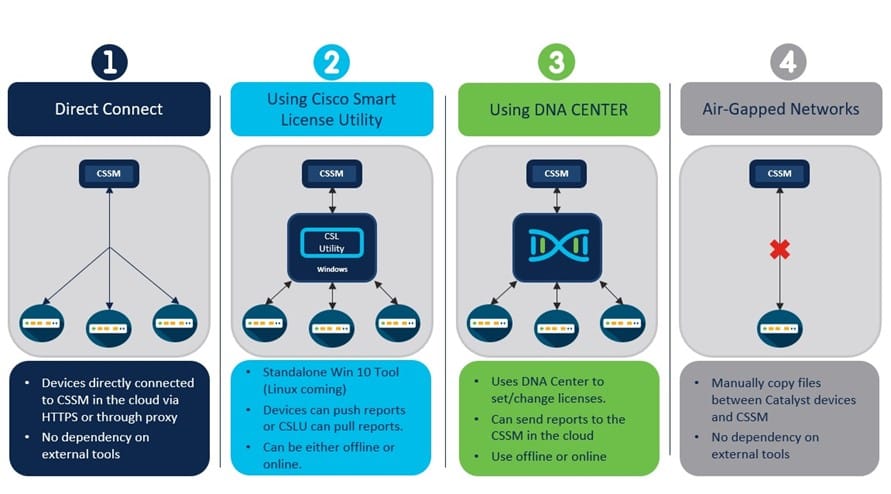
The vulnerable CSLU is a crucial component for managing Cisco software licenses, enabling organizations to activate and track their software deployments. Exploitation of this vulnerability could grant attackers the ability to manipulate license entitlements, potentially disrupting network operations and enabling the deployment of unauthorized software.
The Backdoor in Question: The vulnerability centers around a hardcoded administrative account with default, unchanging credentials present within the CSLU software. This account, effectively a backdoor, bypassed normal authentication procedures, providing a direct route for attackers to gain elevated privileges. The existence of such an account, especially without proper security controls, raises serious questions about Cisco's internal security practices and oversight.
Security experts are urging organizations to immediately verify their CSLU versions and apply the necessary patches provided by Cisco. Failure to do so leaves systems vulnerable to exploitation, potentially leading to significant operational and financial repercussions.
A Pattern of Centralized Control? This incident highlights a growing concern surrounding centralized license management systems. While such systems offer convenience and streamlined administration, they also create a single point of failure and a lucrative target for malicious actors. Critics argue that vendors should prioritize decentralized, more resilient licensing models to mitigate the risks associated with these centralized architectures.
Furthermore, the reliance on proprietary licensing schemes, often tied to specific hardware or software versions, can create vendor lock-in and limit user autonomy. This dependence, combined with vulnerabilities like the CSLU backdoor, underscores the importance of independent security audits and a healthy skepticism towards proprietary solutions, especially those managed by large, centralized entities. Cisco's official website should be consulted for immediate patching information.