CVE-2024-38189: Critical Microsoft Vulnerability Exploit Shared Online by USDoD
Remote code execution (RCE) exploit for a critical Microsoft vulnerability, identified as CVE-2024-38189, has surfaced on a hacker forum. Shared by a user with significant reputation, the Python script targets unpatched systems, potentially allowing attackers to gain full control.
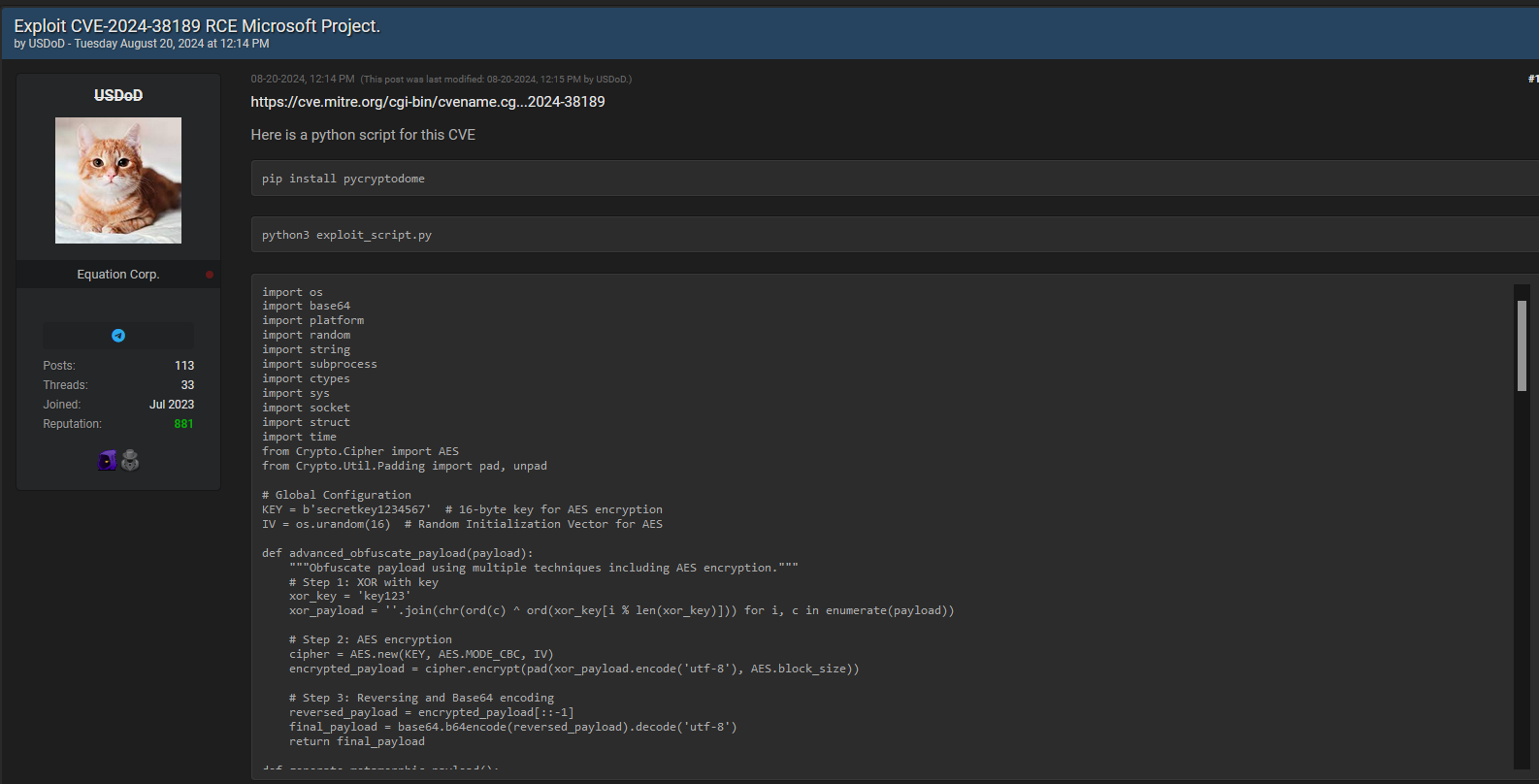
Forum Post Details:
- User: USDoD
- Date and Time: August 20, 2024, at 12:14 PM
- Forum: Equation Corp.
- Reputation: The user has a high reputation score (881), which might indicate they are well-regarded or active within this community.
- Joined: July 2023
Exploit Information:
- CVE Reference: The post includes a link to the CVE entry for this specific vulnerability: CVE-2024-38189.
- Script Purpose: The Python script provided is designed to exploit the vulnerability. The script uses cryptographic techniques (like AES encryption and XOR) to obfuscate the payload, making it harder to detect.
Script Breakdown:
- Imports: The script imports various Python libraries, including
os,base64,random,subprocess, andCrypto.Cipherfor AES encryption. - Global Configuration:
- Key and IV: A static key (
b'secretkey1234567') and a randomly generated initialization vector (IV) are used for AES encryption.
- Key and IV: A static key (
- Functions:
advanced_obfuscate_payload: This function obfuscates the payload by:- XORing it with a key.
- Encrypting the result using AES in CBC mode.
- Reversing and base64 encoding the final payload.
- Other Functions: Though not fully visible, the script likely contains functions to generate and send the payload to a target system.
Implications:
This post indicates a potentially severe security risk, as the script is tailored to exploit a known vulnerability in Microsoft software. If used maliciously, this could result in unauthorized remote access, data theft, or system compromise.
Recommendations:
- Immediate Patch: Ensure that all systems are updated with the latest patches from Microsoft to protect against CVE-2024-38189.
- Monitoring: Increase monitoring for unusual activity that might indicate an exploit attempt using this or similar scripts.
- Education: Raise awareness within the organization about this vulnerability and the potential threats associated with it.




