Cybersecurity Firm CrowdStrike Suffers Significant Breach – 100,000 IoCs Leaked
CrowdStrike suffers a major breach as 100K IoCs are leaked by hacker USD0D in retaliation for alleged false accusations. What does this mean for the cybersecurity giant? #DataBreach #Cybersecurity #CrowdStrike
Company Overview: CrowdStrike
CrowdStrike is a leading cybersecurity firm known for its cutting-edge threat intelligence and endpoint protection services. The company has been instrumental in defending against cyber threats for organizations globally, providing real-time threat detection, analysis, and response.
Breach Details
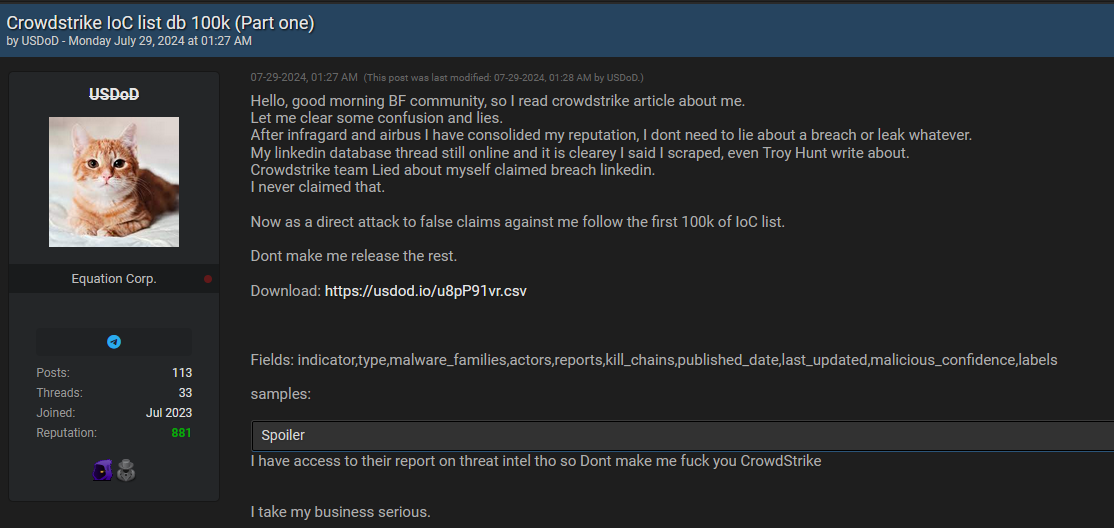
- Date of Incident: July 29, 2024
- Threat Actor: USD0D
- Leak Details:
- Content: The threat actor, USD0D, publicly released a partial list containing 100,000 Indicators of Compromise (IoCs) allegedly from CrowdStrike’s internal threat intelligence database.
- Fields Included: The leak includes data fields such as
indicator,type,malware_families,actors,reports,kill_chains,published_date,last_updated,malicious_confidence, andlabels. - Access Point: USD0D provided a link to download the CSV file directly via a forum post.
- Motivation: According to the post, USD0D claims this release is in response to alleged false accusations made against them by CrowdStrike, specifically regarding the scraping of LinkedIn databases. USD0D asserts that this leak is a warning, with the potential to release more data if provoked further.
Threat Actor Profile: USD0D
- Background: USD0D is an active member of a hacking forum known for leaks and breaches, with a reputation score of 881. They have been involved in multiple high-profile incidents, including those targeting infrastructure and major corporations.
- Motives: The actor seems motivated by a combination of personal vendetta and a desire to showcase power within the cybersecurity space, threatening further leaks if demands or grievances are not addressed.
Impact Analysis
- Potential Impact on CrowdStrike:
- Reputation Damage: The leak could severely damage CrowdStrike’s reputation as a reliable cybersecurity provider, raising questions about their internal security measures.
- Client Trust: Disclosure of sensitive IoCs could lead to a loss of trust from clients who rely on CrowdStrike for protecting their own infrastructures.
- Operational Risk: The leak could compromise ongoing investigations, with threat actors potentially altering their tactics to evade detection based on the exposed IoCs.
- Broader Cybersecurity Risks:
- The leaked IoCs may empower other threat actors by providing them with detailed insights into detection mechanisms, possibly leading to an increase in undetected cyber attacks.




