Daily Dread Drip - Don't Trust Verify
Does Hugbunter's post really validate the Bohemia admin arrest, or is it more darknet speculation? We explore the gaps in evidence and the unrelated focus of Operation Endgame. #DarknetMarkets #Bohemia #VerifyDontTrust
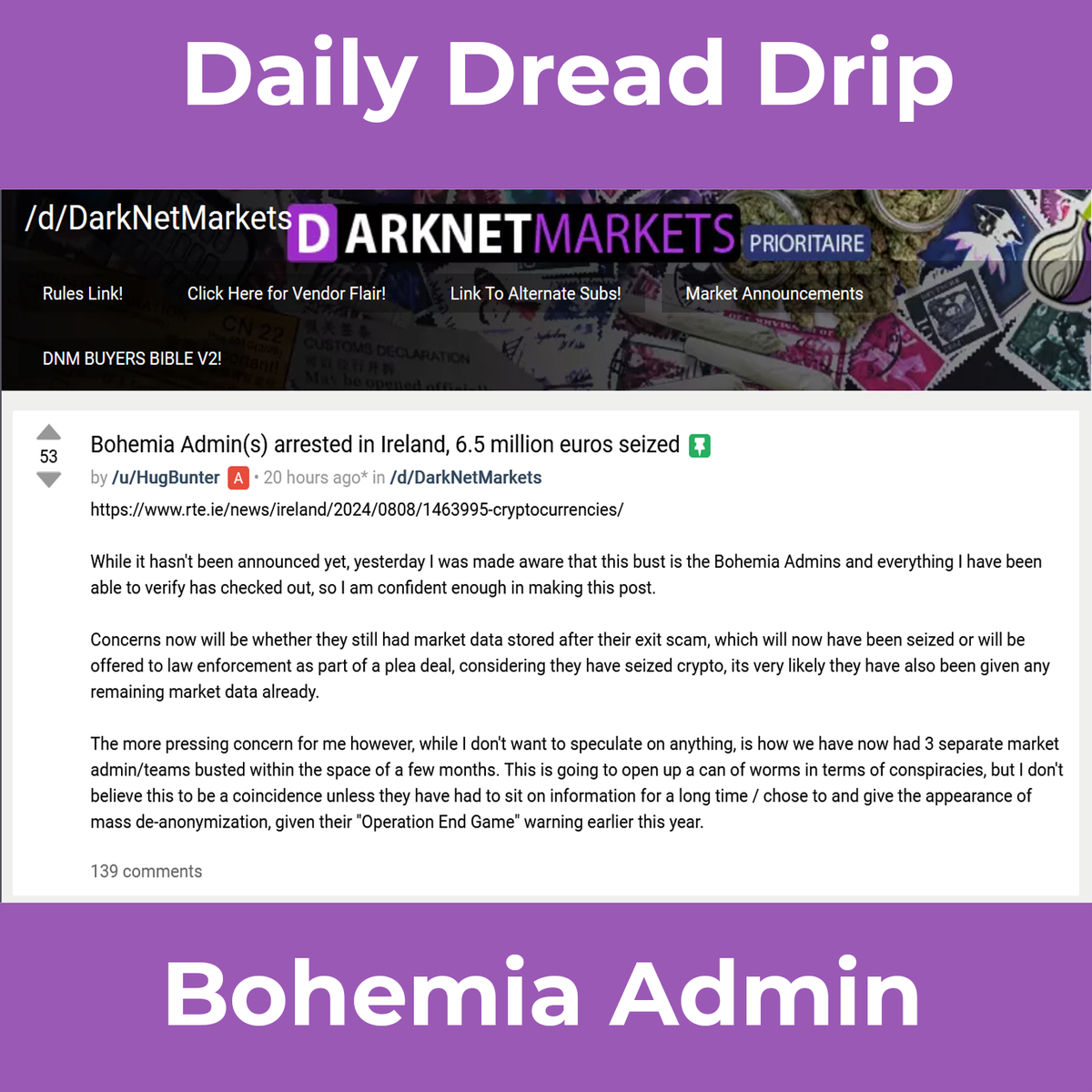
At this point, I've known Hugbunter for about 8 or 9 years. I knew him before Dread existed. One thing I can say definitively is that much of the time, he's correct. I have a ton of respect for him/her (who knows?), Hugbunter (from now on we will call 'HB'), has volunteered his time, for damn near a decade to running:

Dread (Mirror, Mirror) - one of the most popular darknet forums, and one of the most well run. Think of it like Reddit for the darknet. I think it's actually better than Reddit.
Daunt (Clearnet link, Onion Link) - Daunt is an authenticated link directory for multiple darknet markets and interesting onions. This site has validation like no other, though, and some crazy scalability.
Recon (Dead onion) - Recon is the darknet market search engine.
HB has donated almost a decade to this subculture. If anyone deserves the benefit of the doubt, it's HB. That said, the primary response from anyone should be to:
Don't Trust Verify
This post does not take the position that HB is wrong; it's about pointing out that verification in this particular situation is lacking, which is why it is coming to you as NOT taking the position that HB is wrong a post and not a video.
That said, even that is kind of understandable given that facts at the onset of cases like this can also be lacking so verification can be difficult to impossible.
Some of the things that I found inaccurate or unconfirmable were as follows:
Hugbunter’s post regarding the alleged Bohemia admin bust presents several things that point to me that this 'news' is not something that has been completely vetted.
1. Lack of Direct Evidence: Hugbunter claims that the recent bust in Ireland involves the Bohemia admins and asserts that he has "verified" this information. However, he fails to provide direct evidence or explain how this verification was conducted. In the darknet community, where accurate information is crucial for survival, such unsubstantiated claims are a significant red flag. Without concrete proof or verifiable sources, his assertions remain speculative at best. The principle of "verify, don’t trust" is foundational in these circles, and Hugbunter’s failure to adhere to this principle undermines the credibility of his entire post. Undoubtedly, he has led the community for such a long time that he may feel he has no obligation to detail such things as the facts that were verified.
2. Ambiguity in Verification Process: The phrase "everything I have been able to verify has checked out" is vague and leaves much to be desired regarding transparency. Hugbunter does not clarify what "everything" includes—whether it involves cross-referencing, insider information, or analysis of darknet activity. This lack of clarity makes it impossible for readers to assess the reliability of the information themselves. In a community where the accuracy of information can be the difference between safety and exposure, such ambiguity is a critical flaw, in my opinion. I would have much preferred that this be given upfront. Without a clear methodology, the claim of verification is essentially meaningless. Again, HB IS typically at the forefront of news, so I personally would trust his/her word; however, just because I may trust him does not mean that as a journalist or content creator, I would put my reputation up to back up speculation of anyone. I personally would trust his/her word
3. Speculative and Unsubstantiated Conclusions: Despite his claims of verification, Hugbunter delves into speculation when discussing the potential outcomes of the bust, such as whether the admins retained market data or if this data has been seized. He further speculates a possible connection to broader law enforcement actions, including Europol's "Operation End Game." This blending of supposed verification with conjecture creates a confusing narrative where it's difficult to distinguish between what is known and what is merely guessed. The absence of clear, substantiated conclusions further weakens the credibility of his post. By mixing speculation with supposed facts, Hugbunter muddies the waters, making it challenging for his audience to discern the truth.
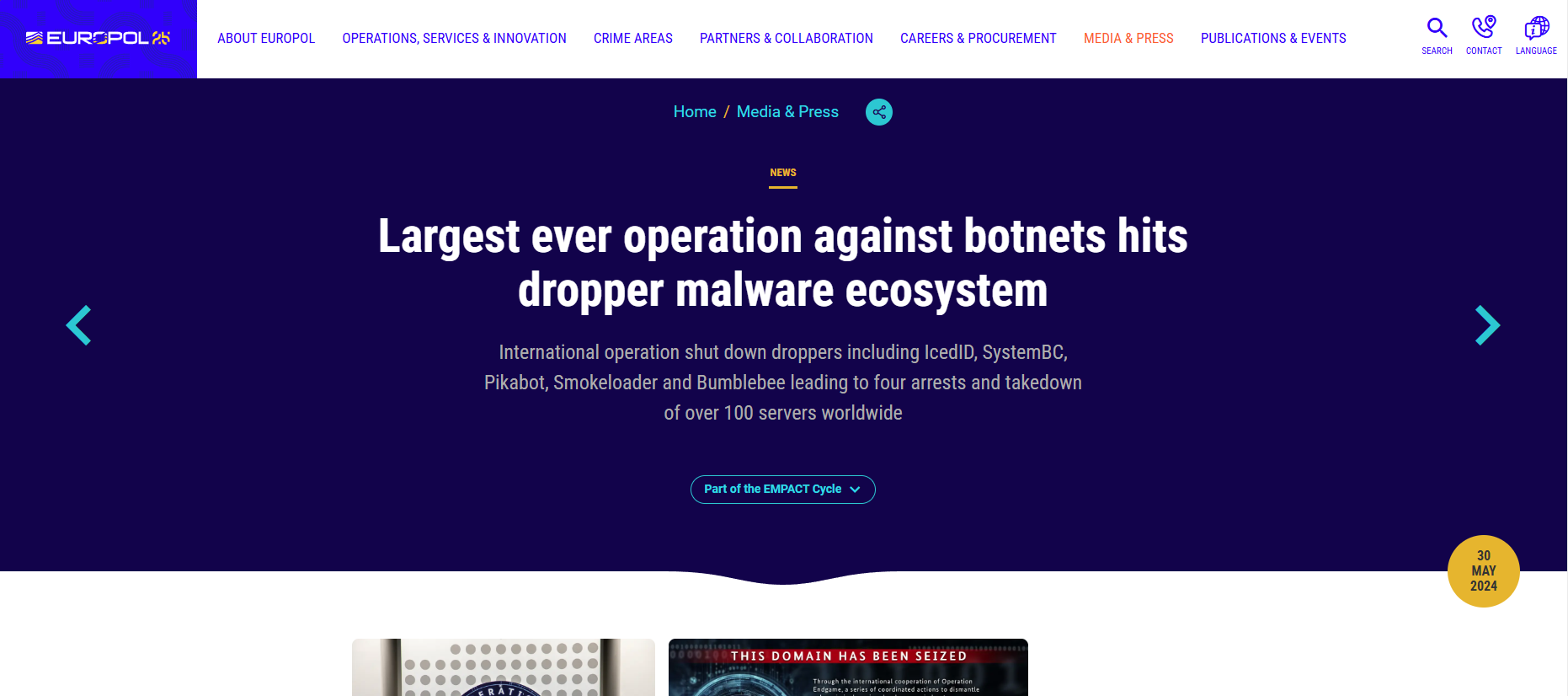
4. Misrepresentation of Operation End Game: Hugbunter’s attempt to connect the Bohemia bust with Europol’s "Operation End Game" is another significant red flag. Operation End Game has been primarily focused on disrupting botnets, malware droppers, and loaders—cybercrime activities largely unrelated to darknet markets. By suggesting a connection without any supporting evidence, Hugbunter misrepresents the scope of Operation End Game at least according to Europol's official statements. This misrepresentation can lead to unnecessary fear and confusion within the community, as it implies a coordinated crackdown on darknet markets where none has been proven to exist.
Operation Endgame was a significant coordinated effort involving law enforcement agencies across multiple countries, including the United States, Denmark, France, Germany, and several others. This operation targeted infrastructure responsible for distributing malware such as IcedID, Trickbot, Smokeloader, and Bumblebee. These malware families were known for infecting millions of computers globally, facilitating ransomware attacks, and causing widespread damage to critical infrastructures like healthcare systems (europol.europa) (Enterprise Technology News and Analysis) (Federal Bureau of Investigation).
5. Lack of Historical Precedent for Mass De-Anonymization: Hugbunter implies that recent darknet market busts might be part of a broader effort involving mass de-anonymization tools by law enforcement.
but I don't believe this to be a coincidence unless they have had to sit on information for a long time / chose to and give the appearance of mass de-anonymization
However, history shows that such a scenario is unlikely. There has never been a time when law enforcement possessed a secret weapon or mass de-anonymization tool that allowed them to simultaneously bring down multiple darknet markets. Instead, most successful takedowns have resulted from simple operational security (OpSec) failures by the administrators themselves.
For instance, the takedown of AlphaBay and Hansa in 2017 was not due to any advanced de-anonymization technique but rather due to specific OpSec mistakes by the administrators—such as the failure to properly secure servers and the use of identifiable personal information (PortSwigger Security) (Wikipedia). Similarly, in the case of Silk Road, Ross Ulbricht's failure to maintain anonymity led to his capture when he was arrested while logged into the Silk Road administration panel (PortSwigger Security). These cases highlight that the downfall of darknet markets is often due to human error rather than sophisticated law enforcement tools.
While Hugbunter’s post might resonate with some as an intriguing piece of darknet gossip, the lack of clear evidence, the unrelated focus of Operation Endgame on malware rather than darknet markets, and the lack of historical precedent for mass de-anonymization underscore the need for caution. This post exemplifies why the darknet community must adhere strictly to the "verify, don’t trust" ethos.




