Evolving TDS Tactics Outpace Defenses, Raising Cybersecurity Alarm
Independent cybersecurity analysts are sounding the alarm over the increasingly sophisticated use of Traffic Distribution Systems (TDS) by malicious actors.
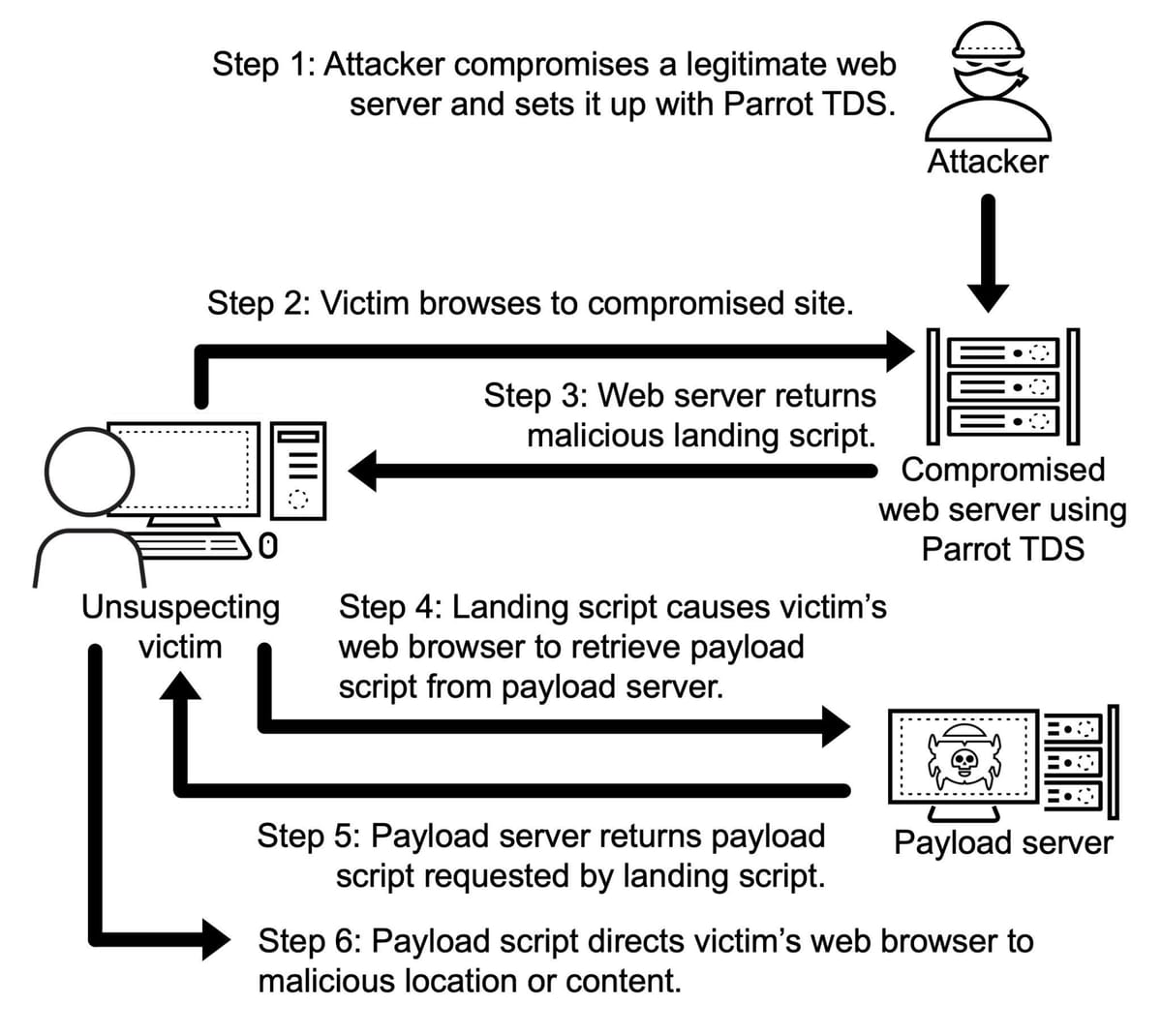
Independent cybersecurity analysts are sounding the alarm over the increasingly sophisticated use of Traffic Distribution Systems (TDS) by malicious actors. These systems, originally designed to efficiently manage and route internet traffic, are now being weaponized in ways that are proving exceedingly difficult to detect and neutralize.
TDS abuse allows threat actors to filter and redirect traffic, serving malicious content only to specific, targeted users. This precision targeting avoids detection by broad-based security measures, making traditional blocklists and signature-based detection methods increasingly ineffective. For example, attackers can use TDS to ensure that malicious payloads are only delivered to users accessing a website from a specific geographic location or using a particular browser version. This makes it significantly harder for security researchers to replicate and analyze the attacks.
"The sophistication we're seeing in TDS deployments is unprecedented," stated an anonymous source within a prominent threat intelligence firm.
Attackers are employing techniques like rotating IP addresses, cloaking their infrastructure behind legitimate services, and using complex filtering rules that rely on user-agent strings, referrer headers, and other contextual data. This makes attribution incredibly challenging and allows malicious campaigns to persist for extended periods undetected.
Experts are urging organizations to adopt more proactive and nuanced security strategies, including:
- Behavioral analysis: Monitoring network traffic for anomalous patterns rather than relying solely on known signatures.
- Threat intelligence sharing: Collaborating with other organizations to share information about emerging TDS tactics and indicators of compromise.
- Improved logging and auditing: Implementing robust logging mechanisms to capture detailed information about network traffic and user activity.
- Zero Trust Architecture: Implementing strict identity verification and access control, limiting the blast radius of any successful attack.
The escalating TDS threat shows the limitations of relying on purely reactive security measures. As threat actors continue to innovate, organizations must adapt their defenses to stay one step ahead. Skepticism towards centralized authorities is growing, with some experts advocating for decentralized and community-driven threat intelligence platforms to counter the increasing sophistication of these attacks.




