i2p
I2P Versions & Essentials
Explore the various I2P versions, each designed for secure, anonymous networking across different platforms and use cases. This page showcases images and links to key I2P software and tools. #I2P #CyberSecurity #PrivacyMatters
20 Aug 2024
— 17 min read
I2P Versions & Essentials
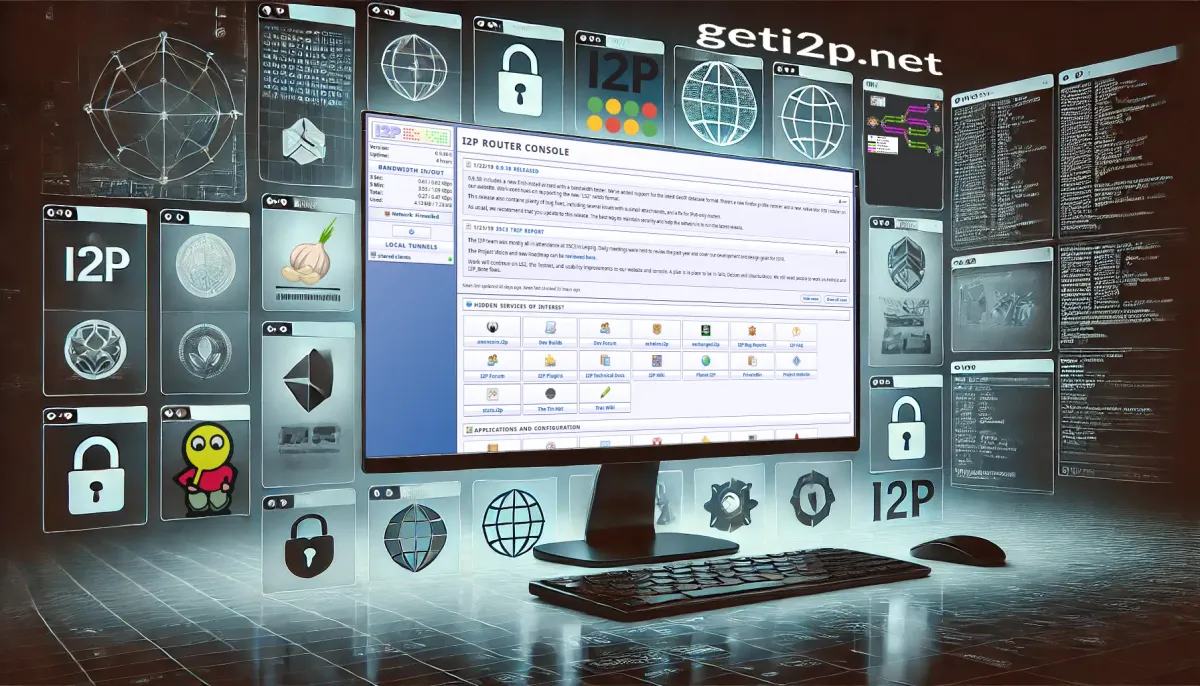
I2P Java (Standard I2P)
Version Name
I2P Java (Standard I2P)
Introduction Year
2003
Unique Features
Original implementation of I2P, written in Java.
Uses garlic routing for enhanced privacy and security.
Supports a wide range of applications, including anonymous websites (Eepsites), messaging, and file sharing.
Fully decentralized with peer-to-peer architecture.
Primary Use Cases
Anonymous browsing and communication.
Hosting anonymous websites (Eepsites).
P2P file sharing.
Secure messaging and chat services.
Security Rank (1-100)
90
Similarities to Other Versions
Shares core security principles with I2Pd and Kovri, including garlic routing and decentralized networking.
Differences from Other Versions
As the original implementation, it is more resource-intensive compared to I2Pd, and lacks some of the optimizations present in later forks like I2P+.
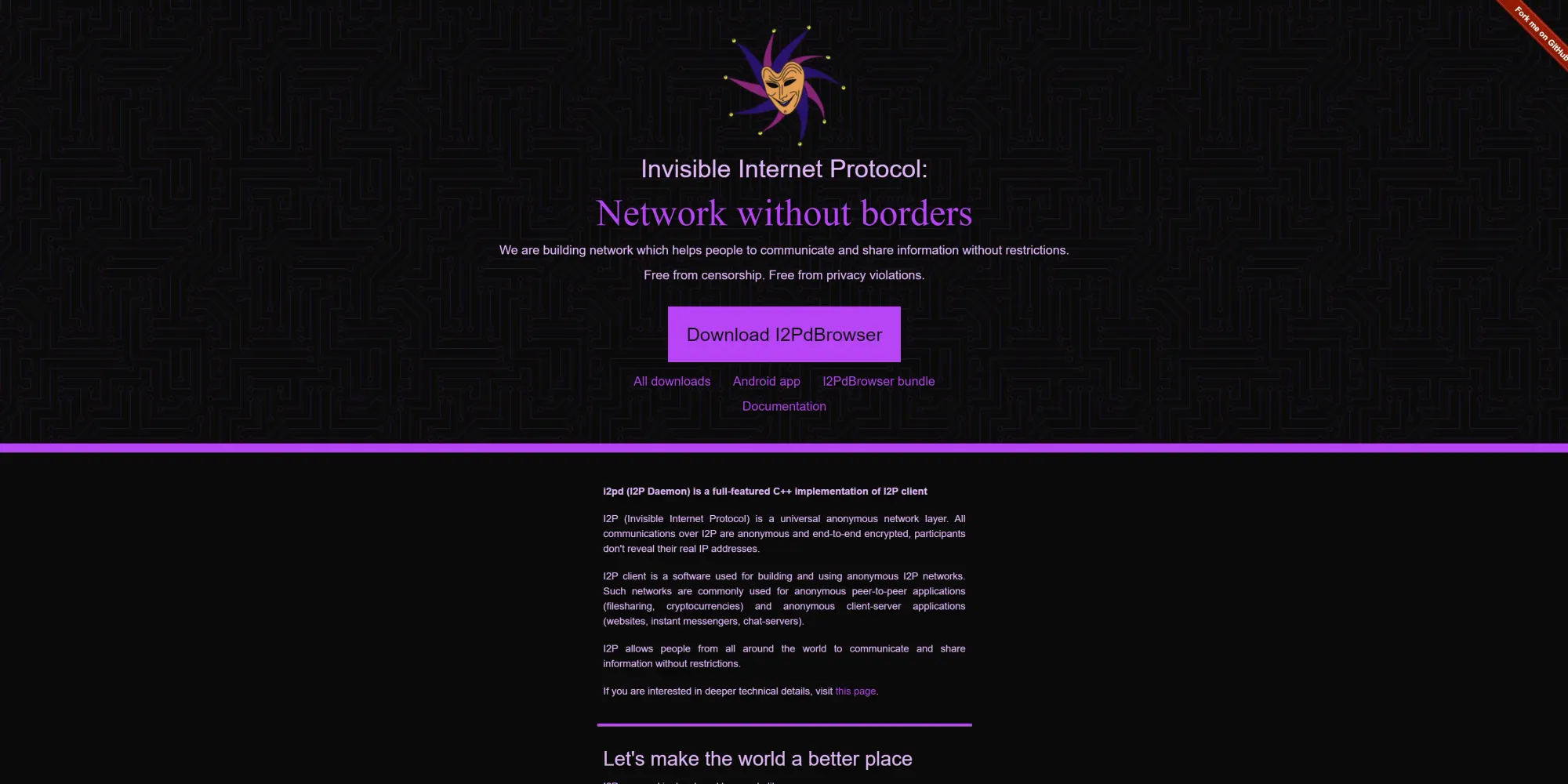
I2Pd (I2P Daemon)
Version Name
I2Pd (I2P Daemon)
Introduction Year
2014
Unique Features
Lightweight and optimized for devices with lower resources, written in C++.
Compatible with the I2P network, allowing it to run on embedded systems and IoT devices.
More efficient memory usage and faster startup times compared to the Java implementation.
Primary Use Cases
Running I2P on lightweight environments like routers, embedded systems, and IoT devices.
Ideal for users requiring lower resource consumption.
Maintains full functionality of the I2P network while being more efficient.
Security Rank (1-100)
88
Similarities to Other Versions
Shares core functionality with the Java version, including garlic routing and the same network protocols.
Differences from Other Versions
Optimized for performance, using less memory and CPU, making it suitable for resource-constrained environments.
Lacks the extensive plugin support of the Java version but compensates with better efficiency.
Kovri
Version Name
Kovri
Introduction Year
2015
Unique Features
Forked from I2Pd by the Monero project, focusing on integrating I2P with cryptocurrency transactions.
Optimized for secure and anonymous Monero transactions, leveraging I2P’s privacy features.
Written in C++ with a focus on efficiency and security.
Primary Use Cases
Anonymous cryptocurrency transactions, particularly for Monero.
Used by privacy-focused applications requiring strong anonymity.
Ideal for users within the cryptocurrency community seeking enhanced privacy.
Security Rank (1-100)
85
Similarities to Other Versions
Shares core functionality with I2Pd, including the use of garlic routing and a focus on efficiency.
Differences from Other Versions
Specifically optimized for cryptocurrency use, particularly Monero, unlike other I2P versions.
Focused more on financial privacy, while other versions target general-purpose anonymity.
I2P+
Version Name
I2P+
Introduction Year
2019
Unique Features
An enhanced fork of the I2P Java version, with improvements in speed, reliability, and resource management.
Focuses on improving performance under high-load conditions while maintaining full compatibility with I2P Java.
Includes a range of optimizations and bug fixes not present in the standard I2P Java version.
Primary Use Cases
Improved P2P file sharing with faster speeds and better resource management.
Used by users who require enhanced performance from their I2P network, particularly in demanding environments.
Suitable for hosting high-traffic Eepsites and other services within the I2P network.
Security Rank (1-100)
87
Similarities to Other Versions
Based on I2P Java, retaining its core features like garlic routing and decentralized networking.
Differences from Other Versions
Includes performance enhancements and bug fixes that improve speed and reliability, which are not present in the standard I2P Java version.
Optimized for scenarios with high network load, offering better resource management.
I2P Android (Google Play)
Version Name
I2P Android (Google Play)
Introduction Year
2012
Unique Features
Mobile version of I2P tailored for Android devices, available through the Google Play Store.
Offers an easy-to-use interface for connecting to the I2P network on mobile devices.
Supports core I2P functionalities such as anonymous browsing, messaging, and file sharing.
Primary Use Cases
Anonymous communication on Android devices.
Accessing Eepsites and other I2P services from a mobile platform.
Convenient for users needing portable, on-the-go access to the I2P network.
Security Rank (1-100)
80
Similarities to Other Versions
Shares core functionality with the I2P Java version, adapted for the mobile environment.
Differences from Other Versions
Optimized for mobile use, with a simpler interface and less intensive resource requirements compared to the desktop versions.
Limited by mobile device capabilities and app store policies, which may restrict some features.
I2P Android (F-Droid)
Version Name
I2P Android (F-Droid)
Introduction Year
2012
Unique Features
Mobile version of I2P available through F-Droid, a repository for free and open-source software.
Offers the same core functionality as the Google Play version but with a focus on privacy and freedom from proprietary software.
Regularly updated with features and improvements aligned with the open-source community's best practices.
Primary Use Cases
Anonymous communication on Android devices for privacy-conscious users.
Accessing I2P services with a focus on using open-source tools.
Ideal for users avoiding Google services or preferring non-proprietary software.
Security Rank (1-100)
82
Similarities to Other Versions
Shares core functionality with the Google Play version and the I2P Java desktop version.
Differences from Other Versions
Distributed through F-Droid, emphasizing open-source principles and user control.
May offer more frequent updates and features that align closely with the broader open-source I2P community.
BiglyBT with I2P
Version Name
BiglyBT with I2P
Introduction Year
2017
Unique Features
Integration of I2P with the BiglyBT BitTorrent client, enabling anonymous torrenting.
Allows users to share and download torrents anonymously through the I2P network.
Offers a seamless experience for users already familiar with the BiglyBT client.
Primary Use Cases
Anonymous torrenting and file sharing through the I2P network.
Ideal for users who prioritize privacy while using torrent clients.
Useful for accessing content within the I2P network securely.
Security Rank (1-100)
85
Similarities to Other Versions
Similar in functionality to I2PSnark (the native I2P torrent client) but integrated within a widely-used BitTorrent client.
Differences from Other Versions
Combines the usability of BiglyBT with the anonymity of I2P, offering a more user-friendly experience compared to standalone I2P torrent clients.
Focuses on file sharing, unlike other I2P versions that are more generalized in their application.
I2P-Browser
Version Name
I2P-Browser
Introduction Year
2017
Unique Features
A browser bundle that integrates the I2P network with a modified Firefox browser.
Designed to make accessing I2P services as easy as possible for users, similar to the Tor Browser for Tor.
Includes pre-configured settings and extensions to ensure secure and anonymous browsing within the I2P network.
Primary Use Cases
Anonymous browsing of I2P services without needing to manually configure a browser.
Ideal for users new to I2P who want a straightforward way to access Eepsites and other I2P resources.
Useful for accessing both I2P-exclusive content and secure connections to the public internet via outproxies.
Security Rank (1-100)
83
Similarities to Other Versions
Similar in concept to the Tor Browser, focusing on ease of use and accessibility for anonymous browsing.
Differences from Other Versions
Specifically tailored for web browsing, unlike other I2P versions that support a broader range of applications.
Includes built-in browser extensions and security settings optimized for I2P use.
I2P-Zone
Version Name
I2P-Zone
Introduction Year
2017
Unique Features
Designed with a focus on usability, featuring a simplified interface tailored for new users.
Streamlines access to the I2P network with fewer configuration steps compared to standard I2P implementations.
Provides a user-friendly experience with a focus on accessibility without compromising core I2P functionalities.
Primary Use Cases
Entry-level anonymous browsing and communication within the I2P network.
Ideal for users who are new to I2P and want a straightforward way to connect and explore.
Useful for accessing I2P services with minimal setup and configuration.
Security Rank (1-100)
75
Similarities to Other Versions
Shares core functionalities with I2P Java, but with a focus on simplifying the user experience.
Differences from Other Versions
Offers a more user-friendly interface with fewer options, making it less intimidating for beginners.
Provides a simplified setup process, but may lack some advanced features available in other versions.
I2P-Bote
Version Name
I2P-Bote
Introduction Year
2011
Unique Features
A secure and anonymous email system that operates within the I2P network.
Uses end-to-end encryption and distributed hash tables for secure, serverless email storage.
Messages are automatically encrypted and digitally signed, ensuring privacy and authenticity.
Primary Use Cases
Anonymous email communication within the I2P network.
Ideal for users needing secure and private messaging, particularly activists, journalists, and privacy advocates.
Used as a plugin within I2P or as a standalone application for secure email communication.
Security Rank (1-100)
80
Similarities to Other Versions
Operates within the I2P network like other versions, but focuses exclusively on secure messaging.
Differences from Other Versions
Designed specifically for email communication, unlike other versions which support a broader range of applications.
Utilizes distributed storage for emails, eliminating the need for centralized servers.
Syndie
Version Name
Syndie
Introduction Year
2006
Unique Features
A distributed, decentralized forum system that operates within the I2P network.
Allows users to create and participate in anonymous forums with strong privacy protections.
Supports a range of content, including text, images, and multimedia, all shared anonymously.
Primary Use Cases
Anonymous discussion forums, where users can exchange information without revealing their identities.
Ideal for privacy-conscious communities and individuals discussing sensitive topics.
Useful for distributing information securely and privately within the I2P network.
Security Rank (1-100)
78
Similarities to Other Versions
Operates within the I2P network like I2P-Bote but focuses on forum-based content rather than email communication.
Differences from Other Versions
Specialized for forum-based discussions, unlike other I2P versions that handle broader communication methods.
Supports a wide range of media types, making it versatile for different types of content.
Transmission-I2P
Version Name
Transmission-I2P
Introduction Year
2015
Unique Features
An anonymous BitTorrent client integrated with I2P, allowing for secure and private torrenting.
Based on the popular Transmission BitTorrent client but modified to operate within the I2P network.
Provides built-in anonymity features, ensuring that torrenting activities are untraceable.
Primary Use Cases
Anonymous file sharing through the I2P network, ensuring privacy and security.
Ideal for users who need to share and download torrents without revealing their identity or IP address.
Useful for accessing torrents that are distributed exclusively within the I2P network.
Security Rank (1-100)
84
Similarities to Other Versions
Similar in functionality to BiglyBT with I2P, focusing on anonymous torrenting but based on the Transmission client.
Differences from Other Versions
Focused specifically on torrenting, with the anonymity features of I2P built directly into the client.
Offers a simpler interface compared to other I2P-integrated torrent clients like BiglyBT.
Taho-LAFS over I2P
Version Name
Taho-LAFS over I2P
Introduction Year
2011
Unique Features
A secure, decentralized cloud storage system that operates over the I2P network.
Distributes data across multiple servers, ensuring privacy and redundancy.
Even if some servers fail or are compromised, the system continues to function securely.
Primary Use Cases
Secure, anonymous data storage with strong privacy protections.
Ideal for users who need to store sensitive data without relying on a single, potentially vulnerable server.
Useful for distributed applications that require secure and private storage solutions.
Security Rank (1-100)
86
Similarities to Other Versions
Operates within the I2P network like other versions, but focused on cloud storage rather than communication or file sharing.
Differences from Other Versions
Specialized for decentralized cloud storage, providing a unique use case compared to other I2P versions.
Emphasizes redundancy and privacy, ensuring data remains secure even if some servers are compromised.
Nightweb
Version Name
Nightweb
Introduction Year
2013
Unique Features
A mobile application designed to provide access to the I2P network on Android devices.
Combines social networking features with anonymous communication, enabling users to share content and communicate securely.
Offers a built-in browser and messaging system, all within the I2P framework.
Primary Use Cases
Anonymous social networking and content sharing on mobile devices.
Ideal for users who require secure and private communication on the go.
Useful for accessing I2P services via a mobile platform with integrated social features.
Security Rank (1-100)
70
Similarities to Other Versions
Shares core functionality with other mobile I2P applications but is unique in its focus on social networking.
Differences from Other Versions
Emphasizes social networking features, unlike other I2P versions that focus primarily on anonymous browsing or file sharing.
Built specifically for mobile use, with features that cater to social interaction in an anonymous environment.
iMule
Version Name
iMule
Introduction Year
2007
Unique Features
An anonymous file-sharing client that uses I2P for secure and private transfers.
Based on the eMule project but modified to operate within the I2P network.
Supports anonymous P2P file sharing with a focus on privacy and security.
Primary Use Cases
Anonymous P2P file sharing within the I2P network.
Ideal for users looking to share and download files securely and privately.
Useful for accessing content within the I2P network with strong privacy protections.
Security Rank (1-100)
75
Similarities to Other Versions
Similar to Transmission-I2P and BiglyBT with I2P in its focus on anonymous file sharing but based on the eMule client.
Differences from Other Versions
Specifically tailored for P2P file sharing with an interface familiar to eMule users.
Operates exclusively within the I2P network, unlike other clients that may offer broader network support.
i2pd-browser
Version Name
i2pd-browser
Introduction Year
2015
Unique Features
A browser bundle based on the i2pd implementation, providing a lightweight alternative to the standard I2P browser.
Offers similar functionalities as the I2P-Browser but optimized for users running i2pd.
Includes pre-configured settings to ensure secure and anonymous browsing within the I2P network.
Primary Use Cases
Anonymous browsing of I2P services with a focus on efficiency and low resource usage.
Ideal for users running i2pd who need a compatible browser solution.
Useful for accessing I2P services securely with a lightweight browser option.
Security Rank (1-100)
82
Similarities to Other Versions
Similar in functionality to I2P-Browser but optimized for use with the i2pd implementation.
Differences from Other Versions
Optimized for the i2pd environment, offering a more lightweight and efficient browsing experience.
Lacks some of the more extensive features found in the standard I2P-Browser, focusing instead on performance and efficiency.
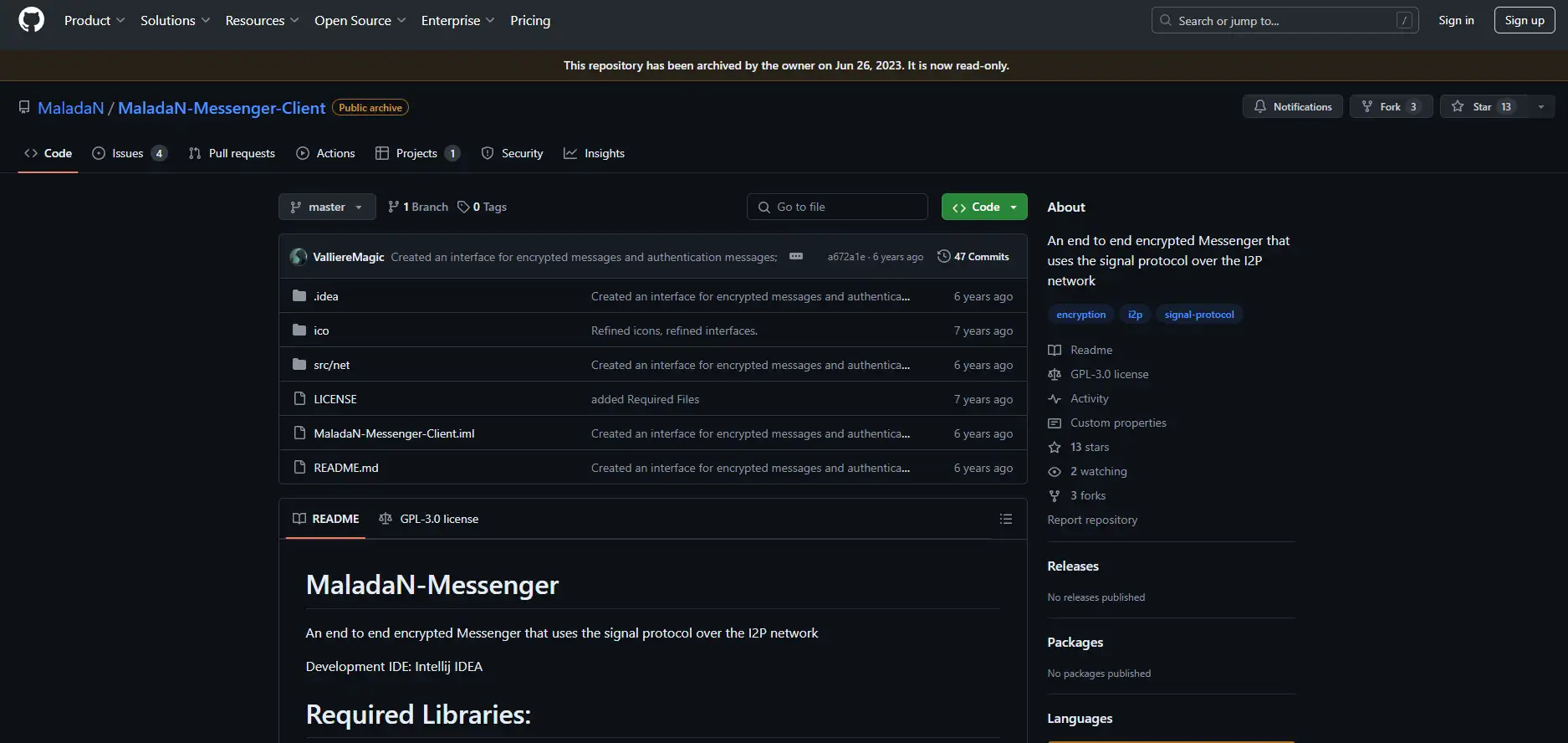
MaladaN-Messenger-Client
Version Name
MaladaN-Messenger-Client
Introduction Year
2017
Unique Features
An end-to-end encrypted messaging client that operates over the I2P network, ensuring secure and private communication.
Uses the Signal protocol, known for its strong encryption, for messaging over I2P.
Focuses on providing a secure messaging platform within the I2P ecosystem, catering to privacy-conscious users.
Primary Use Cases
Secure, anonymous messaging within the I2P network.
Ideal for users who require strong encryption and privacy protections for their communications.
Used for confidential conversations that require a high level of security.
Security Rank (1-100)
88
Similarities to Other Versions
Shares the same focus on secure communication as I2P-Bote, but emphasizes instant messaging rather than email.
Differences from Other Versions
Specializes in real-time messaging using the Signal protocol, unlike other I2P versions that focus on different types of communication.
Designed specifically as a client-side application for end users within the I2P network.
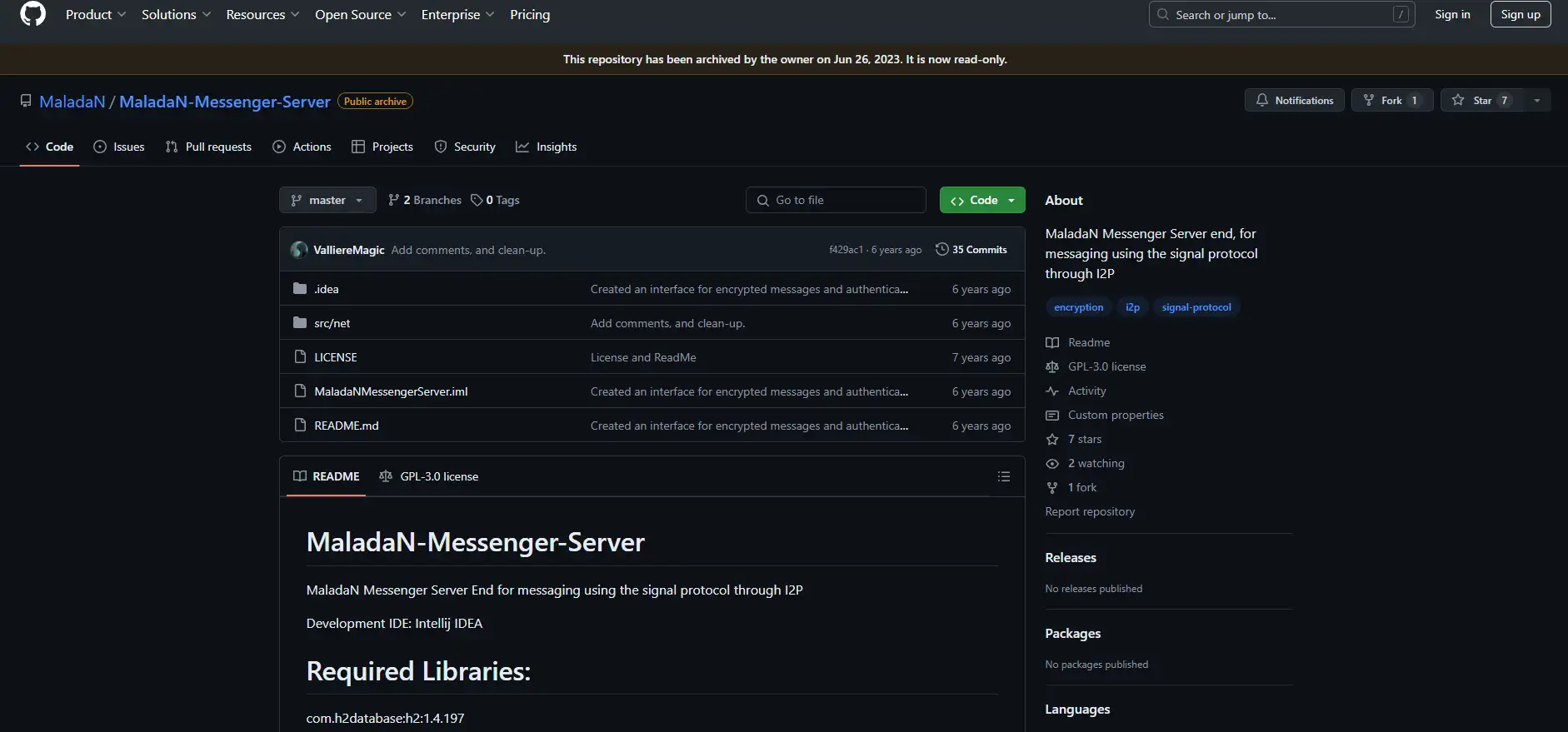
MaladaN-Messenger-Server
Version Name
MaladaN-Messenger-Server
Introduction Year
2017
Unique Features
The server-side component of the MaladaN messaging system, enabling encrypted communication over the I2P network.
Handles the routing and storage of messages, ensuring that all communications remain private and secure.
Designed to work seamlessly with the MaladaN-Messenger-Client, forming a complete secure messaging solution.
Primary Use Cases
Secure server-side management of encrypted messaging within I2P.
Ideal for hosting secure communication services that require strong privacy protections.
Useful for organizations or groups needing a private, secure messaging server within I2P.
Security Rank (1-100)
87
Similarities to Other Versions
Like I2P-Bote's serverless email system, it ensures secure message routing, but focuses on real-time messaging rather than email.
Differences from Other Versions
Works as a server-side application, supporting the MaladaN-Messenger-Client for secure instant messaging.
Handles message storage and routing, ensuring no message is accessible to unauthorized parties.
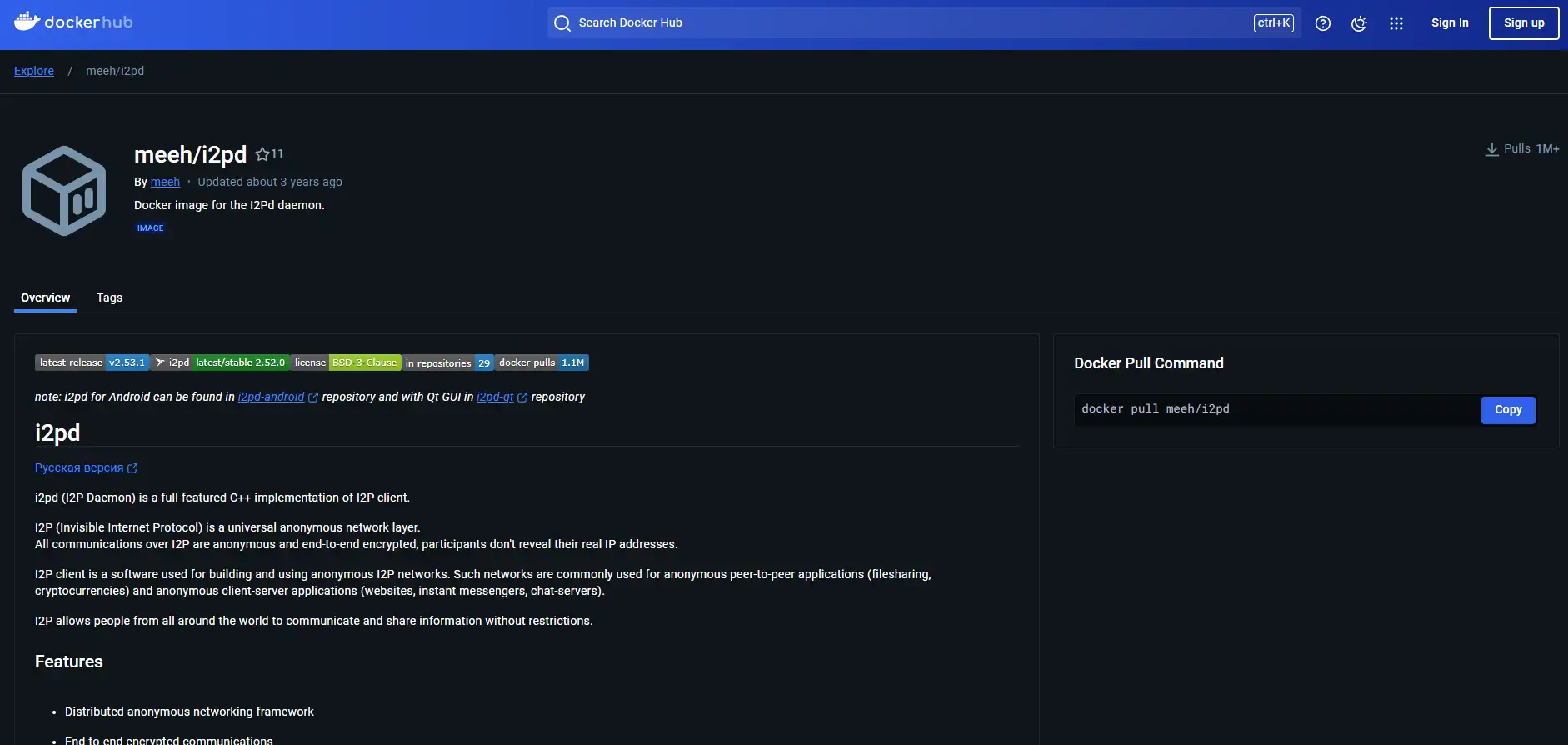
I2P in Docker (meeh/i2pd)
Version Name
I2P in Docker (meeh/i2pd)
Introduction Year
2016
Unique Features
A Docker image designed to run the I2Pd (I2P Daemon) implementation within a containerized environment.
Offers a convenient way to deploy I2P in isolated environments, ensuring consistent and secure setups.
Ideal for users who prefer using Docker for application management and want a simple way to run I2P services.
Primary Use Cases
Running I2P in a containerized environment for easy deployment and management.
Ideal for setting up I2P services in a consistent and reproducible manner across different environments.
Useful for developers and system administrators who want to integrate I2P into their existing Docker-based workflows.
Security Rank (1-100)
85
Similarities to Other Versions
Operates the I2Pd implementation, similar to the standard I2Pd setup, but within a Docker container for easier management.
Differences from Other Versions
Specifically designed to run within Docker, offering unique advantages in deployment and environment isolation.
Focuses on ease of deployment and management, unlike traditional setups that may require more manual configuration.
I2P in Docker (i2p-docker)
Version Name
I2P in Docker (i2p-docker)
Introduction Year
2017
Unique Features
A Docker image designed to run the standard I2P Java implementation within a containerized environment.
Allows for easy deployment and management of I2P in a consistent, reproducible environment using Docker.
Supports all the features of the standard I2P implementation but with the added benefits of containerization, such as isolation and portability.
Primary Use Cases
Running the I2P network in a containerized environment for consistent deployment across different systems.
Ideal for developers and system administrators who want to integrate I2P into their Docker-based infrastructure.
Useful for testing, development, and production environments where isolated and portable setups are required.
Security Rank (1-100)
85
Similarities to Other Versions
Operates the standard I2P Java implementation, similar to a regular I2P setup, but with the benefits of Docker's containerization.
Differences from Other Versions
Specifically designed for containerized environments, offering easy deployment, scalability, and isolation.
Focuses on ease of management and integration with Docker, unlike traditional setups that may require more manual configuration.
i2pberry
Version Name
i2pberry
Introduction Year
2014
Unique Features
A specialized version of I2P designed to run on Raspberry Pi devices, optimizing for low-resource environments.
Provides a lightweight implementation of I2P, ensuring that even low-power devices can participate in the I2P network.
Offers the same core functionalities as the standard I2P Java implementation but tailored for Raspberry Pi’s hardware constraints.
Primary Use Cases
Running I2P on Raspberry Pi for personal, small-scale I2P nodes or services.
Ideal for hobbyists and developers looking to set up a low-cost, low-power I2P node.
Useful for educational purposes and experimentation with decentralized networks on affordable hardware.
Security Rank (1-100)
80
Similarities to Other Versions
Shares the same core functionalities with the standard I2P Java implementation but optimized for lower resource usage.
Differences from Other Versions
Specifically designed for Raspberry Pi, focusing on performance optimization for low-resource environments.
May require additional setup steps tailored to the Raspberry Pi hardware compared to standard desktop or server setups.
pyreseeder
Version Name
pyreseeder
Introduction Year
2015
Unique Features
A Python-based tool designed to manage reseeding for the I2P network, facilitating the distribution of router information to new nodes.
Allows I2P nodes to bootstrap by finding peers more easily, essential for maintaining the network’s decentralization.
Supports the creation, signing, and validation of SU3 files, which are used to securely distribute router information.
Primary Use Cases
Managing and distributing reseed data for I2P, ensuring that new nodes can join the network effectively.
Ideal for administrators of I2P reseed servers who need a reliable tool to maintain network health.
Useful for developers and operators who are involved in maintaining the infrastructure of the I2P network.
Security Rank (1-100)
83
Similarities to Other Versions
Operates similarly to other I2P tools focused on network infrastructure, such as i2p-tools, but specifically targets reseeding functions.
Differences from Other Versions
Specialized for reseeding, unlike other I2P versions and tools that focus on broader network participation or user interaction.
Written in Python, making it accessible and customizable for developers familiar with this language.
I2Pd-Tools
Version Name
I2Pd-Tools
Introduction Year
2016
Unique Features
A set of tools designed to complement the I2Pd implementation of I2P, providing additional functionality and management capabilities.
Includes utilities for managing I2Pd instances, such as controlling configurations, monitoring performance, and enhancing security.
Offers command-line tools that integrate seamlessly with I2Pd for advanced users and administrators.
Primary Use Cases
Managing and optimizing I2Pd instances, particularly in server environments or large-scale deployments.
Ideal for users and administrators who need enhanced control over their I2Pd nodes.
Useful for monitoring and maintaining the health and performance of I2Pd implementations.
Security Rank (1-100)
85
Similarities to Other Versions
Similar to I2P-Tools but specifically designed to integrate with the I2Pd implementation of I2P.
Differences from Other Versions
Focuses exclusively on I2Pd, offering tools that cater to the needs of this specific implementation.
Includes advanced features that may not be necessary or available in other I2P implementations.
GOSTCoin
Version Name
GOSTCoin
Introduction Year
2018
Unique Features
A digital cryptocurrency designed to operate with a focus on privacy and security, leveraging I2P for anonymous transactions.
Uses the GOST cryptographic standards, which are known for their strong security properties, especially within the context of Russian cryptography.
Integrated with I2P to ensure that all transactions are untraceable and secure, providing enhanced privacy over standard cryptocurrencies.
Primary Use Cases
Anonymous cryptocurrency transactions, particularly in regions where privacy is a significant concern.
Ideal for users who prioritize security and anonymity in their financial activities.
Useful for engaging in decentralized finance (DeFi) activities within the I2P network.
Security Rank (1-100)
90
Similarities to Other Versions
Similar to Kovri in its use of I2P for secure, anonymous financial transactions, but with a focus on cryptocurrency.
Differences from Other Versions
Specifically designed as a cryptocurrency, unlike other I2P versions that focus on broader anonymous communication and file sharing.
Employs GOST cryptographic standards, which are less commonly used compared to other cryptographic methods within the I2P ecosystem.
py-i2phosts
Version Name
py-i2phosts
Introduction Year
2017
Unique Features
A Python-based tool designed to manage and update host files for I2P, ensuring that users can easily resolve .i2p addresses within the network.
Automates the process of fetching, verifying, and updating hosts.txt files, reducing manual effort for users and administrators.
Supports integration with custom address books, allowing users to maintain and share their own trusted .i2p addresses.
Primary Use Cases
Maintaining and updating host files within the I2P network to ensure accurate and reliable address resolution.
Ideal for users who manage multiple I2P nodes or those who frequently need to resolve .i2p addresses.
Useful for automating the process of keeping I2P address books up to date.
Security Rank (1-100)
80
Similarities to Other Versions
Similar in purpose to other I2P tools that manage network configurations and address resolutions, but focused on host files specifically.
Differences from Other Versions
Written in Python, making it more accessible for users who prefer Python-based tools and scripts.
Focuses on automating host file management, whereas other tools may cover broader network management tasks.
i2pjump
Version Name
i2pjump
Introduction Year
2017
Unique Features
A web-based service that helps users find and access active .i2p sites by maintaining a directory of known, reliable addresses.
Provides a search and discovery platform within I2P, allowing users to easily navigate the network and discover new resources.
Focuses on helping users quickly find active and trusted .i2p sites, enhancing the overall user experience within the I2P network.
Primary Use Cases
Finding and accessing active .i2p sites within the I2P network.
Ideal for users who are new to I2P and need a straightforward way to discover and access content.
Useful for maintaining a reliable directory of .i2p addresses that can be easily searched and accessed by the community.
Security Rank (1-100)
78
Similarities to Other Versions
Similar to I2P search engines and directories but specifically focused on .i2p sites and their accessibility within the network.
Differences from Other Versions
Specialized for navigating and discovering .i2p addresses, offering a more focused service compared to general search tools.
Provides an easy-to-use interface tailored for the unique structure and challenges of the I2P network.