IntelBroker Strikes Again: $1.5 Billion Japanese Engineering Firm Breached
Access to a $1.5B Japanese engineering firm is up for sale on the dark web. This could have far-reaching consequences. #CyberCrime #DataSecurity
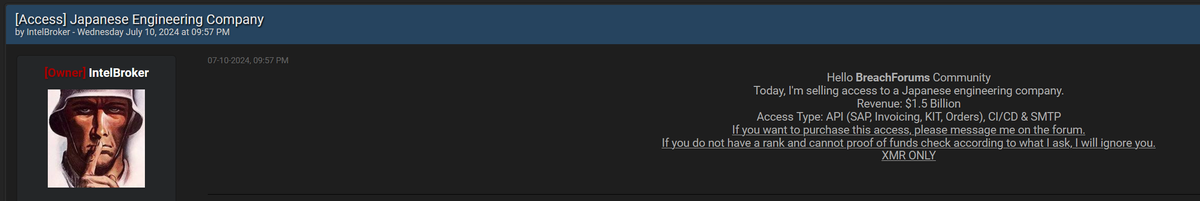
A recent alarming post on a well-known underground forum, BreachForums, has surfaced, revealing the sale of access to a Japanese engineering company with an estimated revenue of $1.5 billion. The post, dated July 10, 2024, was made by a notorious cybercriminal known as "IntelBroker." The hacker, infamous for facilitating access to compromised corporate systems, is offering API access (including SAP, invoicing, orders), CI/CD pipelines, and SMTP services, all for sale to the highest bidder.
Company Overview
The targeted company is a significant player in the Japanese engineering sector, generating over $1.5 billion in revenue annually. Companies of this scale are often deeply integrated into global supply chains, making them attractive targets for cybercriminals seeking access to valuable proprietary information, intellectual property, and other sensitive data.
Japanese corporations have historically been appealing targets for cyber attackers due to their involvement in cutting-edge technology and engineering projects. The high level of automation and reliance on digital infrastructure in the engineering sector means that any breach could have far-reaching consequences, not just for the company itself but also for its clients and partners worldwide.
Breach Details
IntelBroker's post highlights that the breach involves multiple types of access points, including:
- API Access: Access to critical systems like SAP, invoicing, and order processing.
- CI/CD Pipelines: Continuous Integration and Continuous Delivery processes, which could allow attackers to inject malicious code or backdoors into the company’s software development lifecycle.
- SMTP Services: Control over email servers, potentially enabling phishing attacks or the exfiltration of sensitive email communications.
The nature of these access points suggests that the attacker has deep, persistent access to the company's IT infrastructure, potentially acquired through advanced methods such as spear-phishing, exploiting vulnerabilities in third-party software, or insider threats.
Threat Actor Profile: IntelBroker
IntelBroker is a known entity within the cybercriminal community, previously linked to various high-profile breaches. The individual or group behind this alias has a reputation for brokering access to compromised systems, often targeting large corporations with significant revenues. IntelBroker's modus operandi involves leveraging dark web forums like BreachForums to reach a wide audience of potential buyers, often requiring payments in cryptocurrency, such as Monero (XMR), to maintain anonymity.
The fact that IntelBroker has listed this Japanese engineering company as a target is indicative of the threat actor’s focus on high-value targets, likely due to the significant profits that can be made from selling access to such companies.
Context and Historical Breach Information
This incident is not an isolated case in Japan’s corporate sector. Japanese companies have been targeted in several notable cyberattacks in recent years. In 2022, multiple Japanese conglomerates were hit by ransomware attacks, leading to operational shutdowns and significant financial losses. Additionally, there have been cases where sensitive technological data was stolen and later found being sold on dark web marketplaces, much like the scenario described by IntelBroker.
These incidents highlight the growing need for robust cybersecurity measures within Japan's corporate ecosystem, particularly for engineering firms that are increasingly becoming prime targets for sophisticated cybercriminal operations.




