Kraken: All-in-One Toolkit for BruteForce Attacks
Kraken is a powerful, Python-based tool designed to centralize and streamline various brute-forcing tasks. It provides cybersecurity professionals with a comprehensive suite of tools to efficiently perform brute-force attacks across a wide range of protocols and services.
Kraken: A Comprehensive Guide to the Ultimate Brute-Forcing Tool for Cybersecurity Professionals
Kraken is a powerful, Python-based tool designed to centralize and streamline various brute-forcing tasks. It provides cybersecurity professionals, ethical hackers, and penetration testers with a comprehensive suite of tools to efficiently perform brute-force attacks across a wide range of protocols and services. Whether you're targeting network protocols like FTP, SSH, or Telnet, or web applications like WordPress, Joomla, or Office365, Kraken simplifies the process with its user-friendly interface and robust functionality.
This guide will walk you through everything you need to know about Kraken, including its installation, usage, and how to combine it with Tor for enhanced anonymity. We'll also provide detailed examples of syntax and best practices for ethical use.
⚠️ Legal Disclaimer
Kraken is intended for educational and ethical purposes only. Unauthorized use of this tool for malicious purposes is strictly prohibited. The author of Kraken is not responsible for any illegal or unauthorized activities conducted using this tool. Always ensure that you have proper authorization before conducting any security testing or penetration testing. Compliance with local laws and regulations is the sole responsibility of the user.
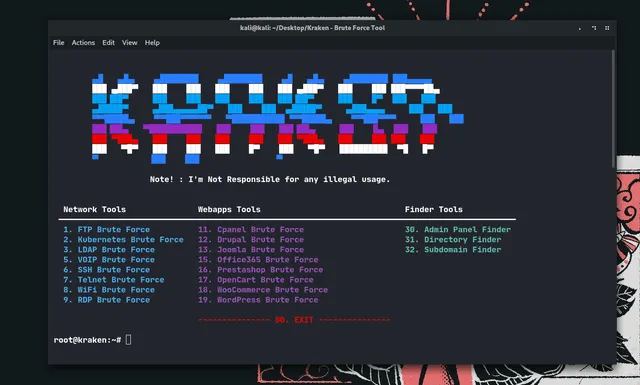
🖥️ Screenshots
While Kraken is a command-line tool, its intuitive menu-driven interface makes it easy to navigate and use. Screenshots of the tool in action can be found on the official Kraken GitHub repository.
⚙️ Installation
Installing Kraken is straightforward. Follow these steps to get started:
Launch Kraken:
python kraken.py
Install the required dependencies:
pip install -r requirements.txt
Navigate to the Kraken directory:
cd kraken
Clone the Kraken repository from GitHub:
git clone https://github.com/jasonxtn/kraken.git
Once installed, you’ll have access to Kraken’s extensive suite of brute-forcing tools.
📖 Usage
Kraken’s tools are categorized into three main sections: Network Tools, Webapps Tools, and Finder Tools. Below is a breakdown of the available tools and how to use them.
Network Tools
- FTP Brute Force
- Kubernetes Brute Force
- LDAP Brute Force
- VOIP Brute Force
- SSH Brute Force
- Telnet Brute Force
- WiFi Brute Force
- WPA3 Brute Force
Webapps Tools
- CPanel Brute Force
- Drupal Brute Force
- Joomla Brute Force
- Magento Brute Force
- Office365 Brute Force
- Prestashop Brute Force
- OpenCart Brute Force
- WooCommerce Brute Force
- WordPress Brute Force
Finder Tools
- Admin Panel Finder
- Directory Finder
- Subdomain Finder
How to Use Kraken
- Follow the on-screen prompts to input the required information, such as the target IP address, username, and wordlist.
- Review the results provided by the tool.
Select the desired tool from the main menu by typing its corresponding number. For example:
root@kraken:~# 1
This command would start the FTP Brute Force tool.
Launch Kraken from the command line:
python kraken.py
🛠️ Example Syntax and Commands
Here are some examples of how to use Kraken for specific tasks:
Example 1: FTP Brute Force
- Launch Kraken and select the FTP Brute Force tool.
- Kraken will attempt to brute-force the FTP login using the provided credentials.
Enter the target IP address, username, and path to the wordlist.
Target IP: 192.168.1.1
Username: admin
Wordlist path: /path/to/wordlist.txt
Example 2: WordPress Brute Force
- Launch Kraken and select the WordPress Brute Force tool.
- Kraken will attempt to brute-force the WordPress login page.
Enter the target URL, username, and wordlist path.
Target URL: http://example.com/wp-login.php
Username: admin
Wordlist path: /path/to/wordlist.txt
🔒 Using Kraken with Tor for Enhanced Anonymity
To use Kraken in combination with Tor for increased anonymity, follow these steps:
- Configure Kraken to route traffic through Tor:
- Edit the Kraken configuration file (if available) to set the proxy settings to use Tor’s SOCKS proxy (
127.0.0.1:9050).
- Edit the Kraken configuration file (if available) to set the proxy settings to use Tor’s SOCKS proxy (
- Verify your anonymity:
Ensure that your IP address is masked by checking it through a service like WhatIsMyIP.
Run Kraken through Tor:
proxychains python kraken.py
Alternatively, use the proxychains tool to route Kraken’s traffic through Tor:
sudo apt-get install proxychains
Install Tor on your system:
sudo apt-get install tor
🌟 Show Your Support
If you find Kraken helpful or interesting, please consider giving it a star on GitHub. Your support helps promote the project and lets others know that it's worth checking out. Visit the official Kraken GitHub repository to show your support.
🚀 Conclusion
Kraken is a versatile and powerful tool for cybersecurity professionals, offering a wide range of brute-forcing capabilities. However, always remember to use it responsibly and ethically. By combining Kraken with tools like Tor, you can enhance your anonymity and ensure secure testing practices.
For more information, visit the official Kraken GitHub repository and explore its full potential. Happy ethical hacking! 🛡️




