Massive Data Breach Hits Mexico City's Superior Court of Justice: Over 300,000 Accounts Compromised
Mexico City's Superior Court of Justice suffers a massive data breach, with over 300,000 accounts compromised. Sensitive legal data from 2017-2024 exposed. #DataBreach #CyberSecurity
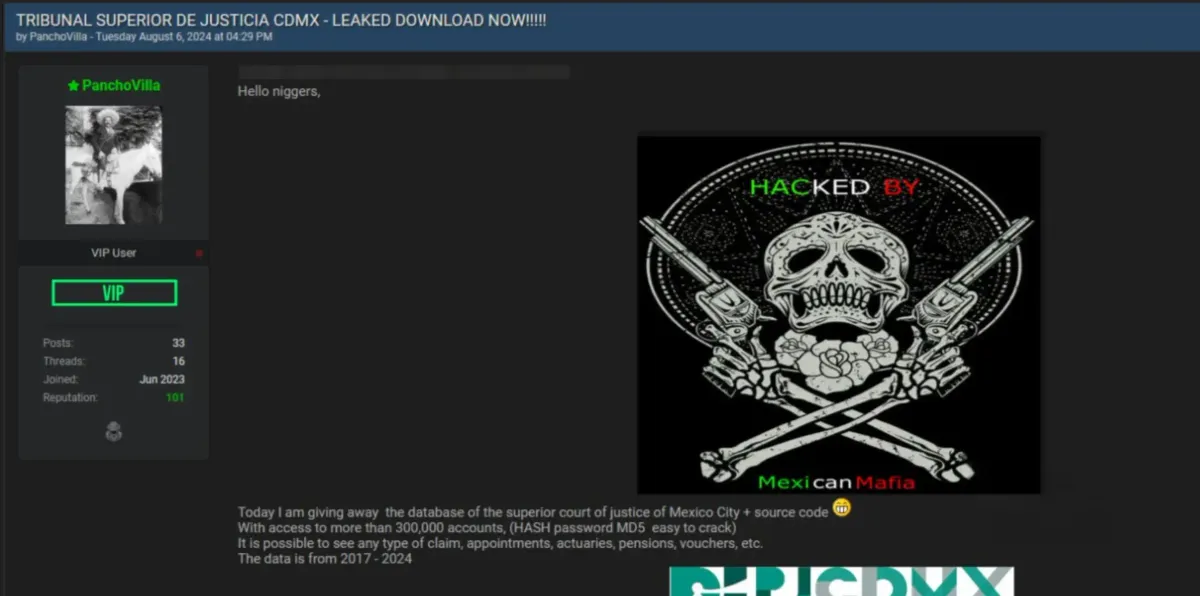
A significant data breach has reportedly occurred involving the Tribunal Superior de Justicia of Mexico City. A threat actor, identified as PanchoVilla, claimed responsibility for the breach on an underground forum, asserting that the compromised data includes over 300,000 accounts with MD5 hashed passwords, which are notoriously easy to crack. The leaked data spans from 2017 to 2024 and includes sensitive information such as claims, appointments, actuaries, pensions, vouchers, and more.
Key Details
Affected Sites:
Content Claimed to be Leaked:
- Database of the Superior Court of Justice of Mexico City
- Source code
- Detailed information on various legal proceedings and user data
The veracity of the data breach claim has not been independently verified, and the information is presented based on the claims made by the threat actor involved.
Breach Details
Nature of the Breach
The data breach involves the Tribunal Superior de Justicia of Mexico City, compromising a significant amount of sensitive information. The threat actor claims to have obtained access to a database containing more than 300,000 accounts. The data includes MD5 hashed passwords, which are weak and susceptible to cracking, making the compromised accounts highly vulnerable.
Scope of Leaked Data
The leaked data reportedly covers a wide range of sensitive information:
- Claims: Legal claims and case details.
- Appointments: Schedules and appointment details within the judicial system.
- Actuaries: Data related to actuarial evaluations.
- Pensions: Information on pension schemes and beneficiaries.
- Vouchers: Financial vouchers and associated details.
The data spans from 2017 to 2024, indicating a long-term compromise of the system.
Source Code
In addition to the database, the threat actor claims to have obtained the source code of the affected systems. This could potentially expose the inner workings of the judicial system's software, making it easier for other malicious actors to exploit vulnerabilities.
Threat Actor Profile
The individual or group behind this breach uses the pseudonym "PanchoVilla," a reference to the famous Mexican revolutionary. The threat actor's profile on the forum indicates they have been active since June 2023, with a moderate reputation and several posts and threads, suggesting a certain level of engagement and credibility within the cybercriminal community.
System Vulnerabilities
The use of MD5 hashing for passwords highlights a significant security weakness. Modern security practices recommend stronger hashing algorithms such as bcrypt or Argon2 to protect passwords.