OPSEC, Origins, Understanding, Process, VS InfoSec, Misconceptions and the NSA
What is OpSec? Who needs OpSec? Where does it come from? How is OpSec Different from InfoSec? What are some OpSec Misconceptions? What is the OpSec Process?

Origins of OPSEC
Operational Security (OPSEC) originated during the Vietnam War as a crucial part of military strategy. It was formally established under the code name "Purple Dragon," (See PDF at the bottom) as a response to the challenges faced by U.S. forces due to significant intelligence leaks that were detrimentally affecting military operations. The program was designed to identify and prevent the leakage of sensitive information that, when pieced together by enemy forces, could reveal significant insights into U.S. military strategies and troop movements.

The creators of OPSEC analyzed how seemingly trivial bits of information, like the timing of supply shipments or the details mentioned in soldiers’ letters home, could be compiled by the enemy to predict military actions. This realization led to the development of procedures aimed at safeguarding this "critical information" from being inadvertently disclosed and used against U.S. forces.
The successful implementation of OPSEC during the war highlighted its effectiveness in protecting sensitive information from adversaries who were actively seeking to exploit any available data. Recognizing its value, the principles of OPSEC were declassified and adapted for wider use beyond the military context.
Today, OPSEC is no longer just military jargon but a fundamental security practice integrated across various sectors, including corporate, government, and private domains. It is employed to protect trade secrets, personal information, proprietary data, and strategic plans. The transition from a military-specific strategy to a universally applicable security measure underscores the versatility and importance of OPSEC in managing and securing sensitive information in an increasingly interconnected world where information leakage can have far-reaching consequences.
Understanding OPSEC
At its core, OPSEC is about identifying and protecting information that, if exposed, could lead to a serious breach of security. It’s essentially about keeping your secrets, well, secret. Here’s how you can implement it (Simple right!?!?):
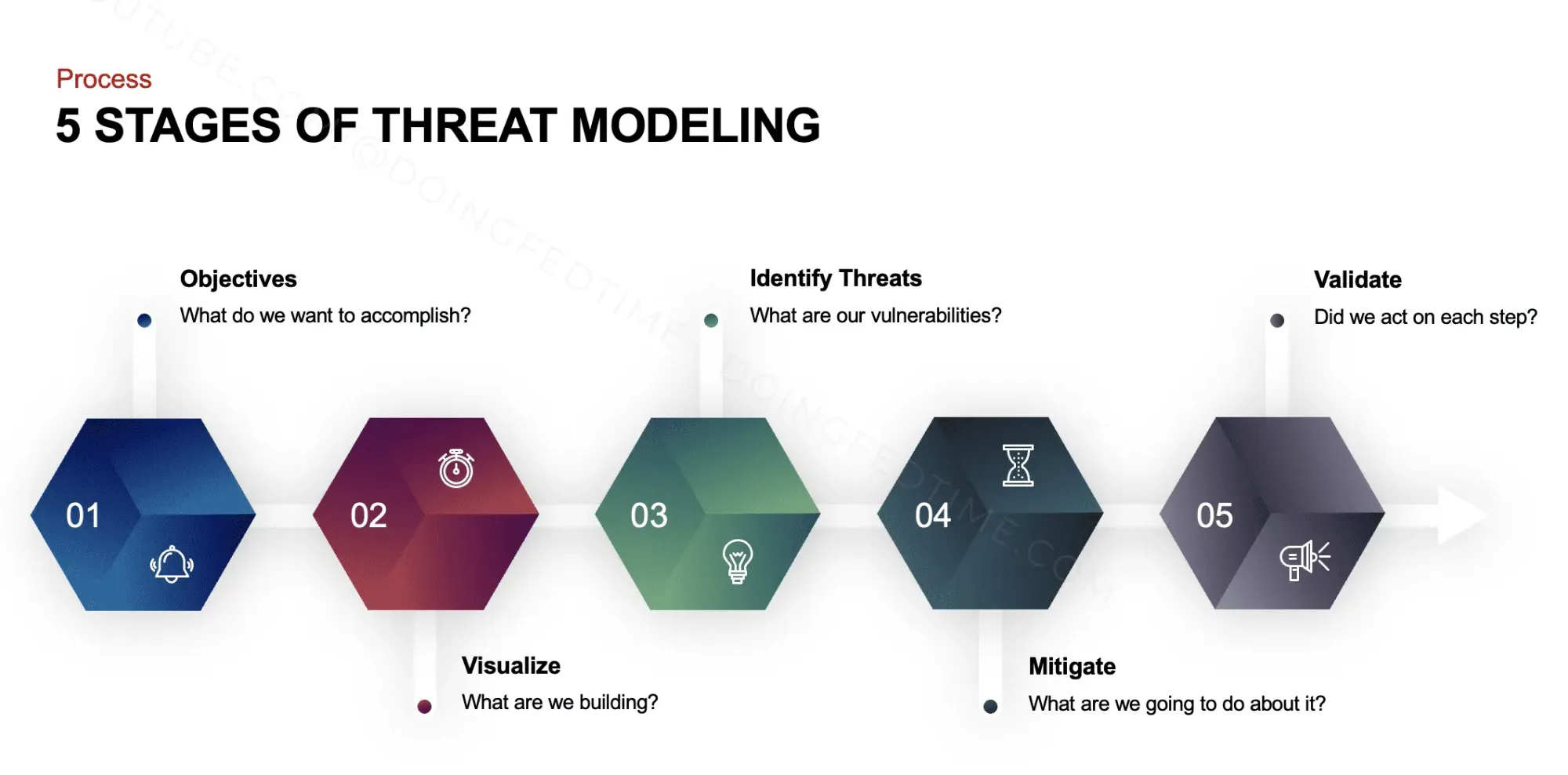
OPSEC Process: A Closer Look
- Identify Critical Information: Start by pinpointing exactly what information is vital and could be harmful if disclosed. This could be personal details, upcoming project plans, or strategic moves in a business.
- Analyze the Threats: Understand who might be interested in your information. This isn’t just about external threats but can also involve insiders or even business partners.
- Analyze Vulnerabilities: Assess the channels through which your information could be accessed. This includes digital vulnerabilities and physical ones, like unsecured documents or conversations overheard in public.
- Assess Risk: Evaluate how likely it is that these vulnerabilities could be exploited and the impact of potential exploitation. This helps prioritize the defenses you need to set up.
- Apply Countermeasures: Implement the necessary strategies to mitigate risks. This could range from encrypting emails to educating employees about the importance of discretion.
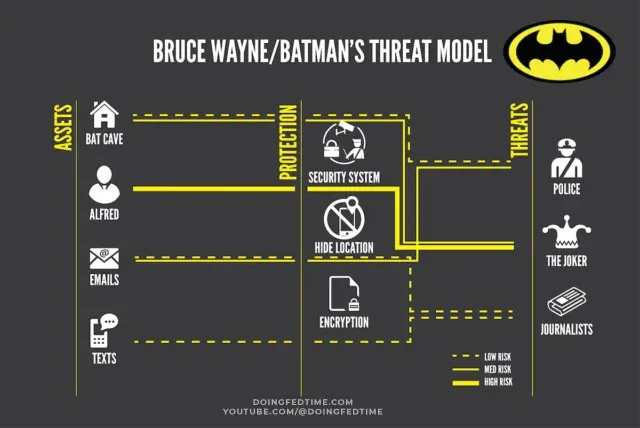
Threat Modeling and Tailoring Your OPSEC
Threat modeling works hand-in-hand with OPSEC by providing a structured approach to identifying potential threats and vulnerabilities. It’s about asking, "What could go wrong?" and "How can we prevent it?" Conduct regular threat modeling sessions to stay ahead of potential threats, and adapt your OPSEC measures as threats evolve.
OPSEC vs. InfoSec
While both OPSEC and Information Security (InfoSec) aim to protect information, OPSEC is broader in scope, focusing on behaviors and processes that cover a range of information types, not just digital. InfoSec is primarily concerned with protecting electronic information through technology and is more technical in approach.
For Everyone
Whether you're just starting to consider your personal information security, or you're a seasoned security professional, OPSEC offers valuable strategies to safeguard your sensitive information. By understanding and applying OPSEC principles, you can significantly enhance your overall security posture.
Common Misconceptions about OPSEC
- OPSEC is only for the military: While its origins are military, the applications today are vast, impacting areas like personal data security, corporate espionage, and social media privacy.
- OPSEC is just about technology: Technology is a tool in OPSEC, but the strategy encompasses behavior, habits, and procedures.
- Once set, OPSEC doesn’t need updating: OPSEC is dynamic. As threats evolve, so must our strategies.
- OPSEC is overly complex: At its core, OPSEC can be as simple as not sharing sensitive information publicly. The complexity grows with the level of threat and the sensitivity of the information.
- Small data leaks are harmless: Small pieces of information can piece together a larger, harmful picture.
- All data is equally valuable: Not all data needs the same level of protection. Part of OPSEC involves assessing which data is most sensitive.
- OPSEC and cybersecurity are the same: Cybersecurity is a subset of OPSEC; OPSEC also covers physical and procedural security measures.




