Over 5,000 Users Affected in Villaments.win Data Leak
Villaments.win has suffered a massive data breach, exposing over a million records. Users are urged to change their passwords and monitor their accounts for suspicious activity. Stay safe! #DataBreach #CyberSecurity
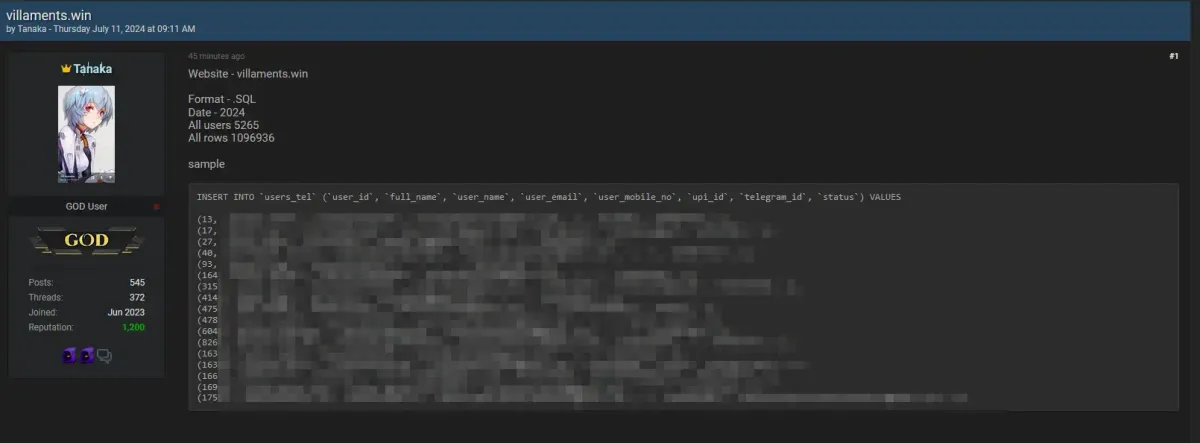
Villaments.win is an online platform offering various digital services. With a user base exceeding 5,000 members, the site caters to a broad audience seeking diverse online experiences.
Breach Details
🔍 Date of Breach: July 11, 2024
🔍 Format: SQL Database
🔍 Data Compromised:
- User IDs
- Full Names
- Usernames
- Email Addresses
- Mobile Numbers
- UPI IDs (Unified Payments Interface)
- Telegram IDs
- Account Statuses
A total of 1,096,936 rows of data were leaked, impacting 5,265 users.
Threat Actor Profile
The breach was disclosed by a user known as Tanaka on a dark web forum. Tanaka holds a reputation as a "GOD User" in the community, indicating a high level of activity and influence. The profile shows:
- Posts: 545
- Threads: 372
- Joined: June 2023
- Reputation: 1,200
Activity: Tanaka is a prominent threat actor known for sharing stolen data on various dark web forums. This individual has been active in the cybercrime community and has gained a reputation for leaking significant datasets.
Notable Activities
- Ayush Jharkhand Database Leak:
- Date: August 14, 2023
- Details: Tanaka leaked a database containing over 320,000 patient records from the Ayush Jharkhand website, including PII and medical diagnoses. The breach also exposed doctors' PII, login credentials, and contact information (CloudSEK | Predicting Cyber Threats) (CybelAngel).
- Recent Activity:
- Date: July 11, 2024
- Details: Tanaka posted a new dataset on a dark web forum, allegedly from Villaments.win, affecting 5,265 users and comprising over a million records. This dataset includes user IDs, full names, usernames, email addresses, mobile numbers, UPI IDs, Telegram IDs, and account statuses (CloudSEK | Predicting Cyber Threats) (CybelAngel).
Methods and Impact
Tanaka operates by infiltrating databases and extracting large volumes of sensitive information. The typical impact of such breaches includes:
- Identity Theft: Exposure of PII can lead to identity theft and fraud.
- Financial Loss: Leaked financial details, such as UPI IDs, can be exploited for unauthorized transactions.
- Phishing Attacks: Email addresses and other contact information can be used to conduct targeted phishing campaigns.