StockZ11.com Data Breach - What you need to know

Company Profile
StockZ11.com is a burgeoning financial technology platform offering insights and resources for stock trading enthusiasts. The service provides users with up-to-date market data, investment tools, and educational content to navigate the often complex world of stock trading.
Breach Details
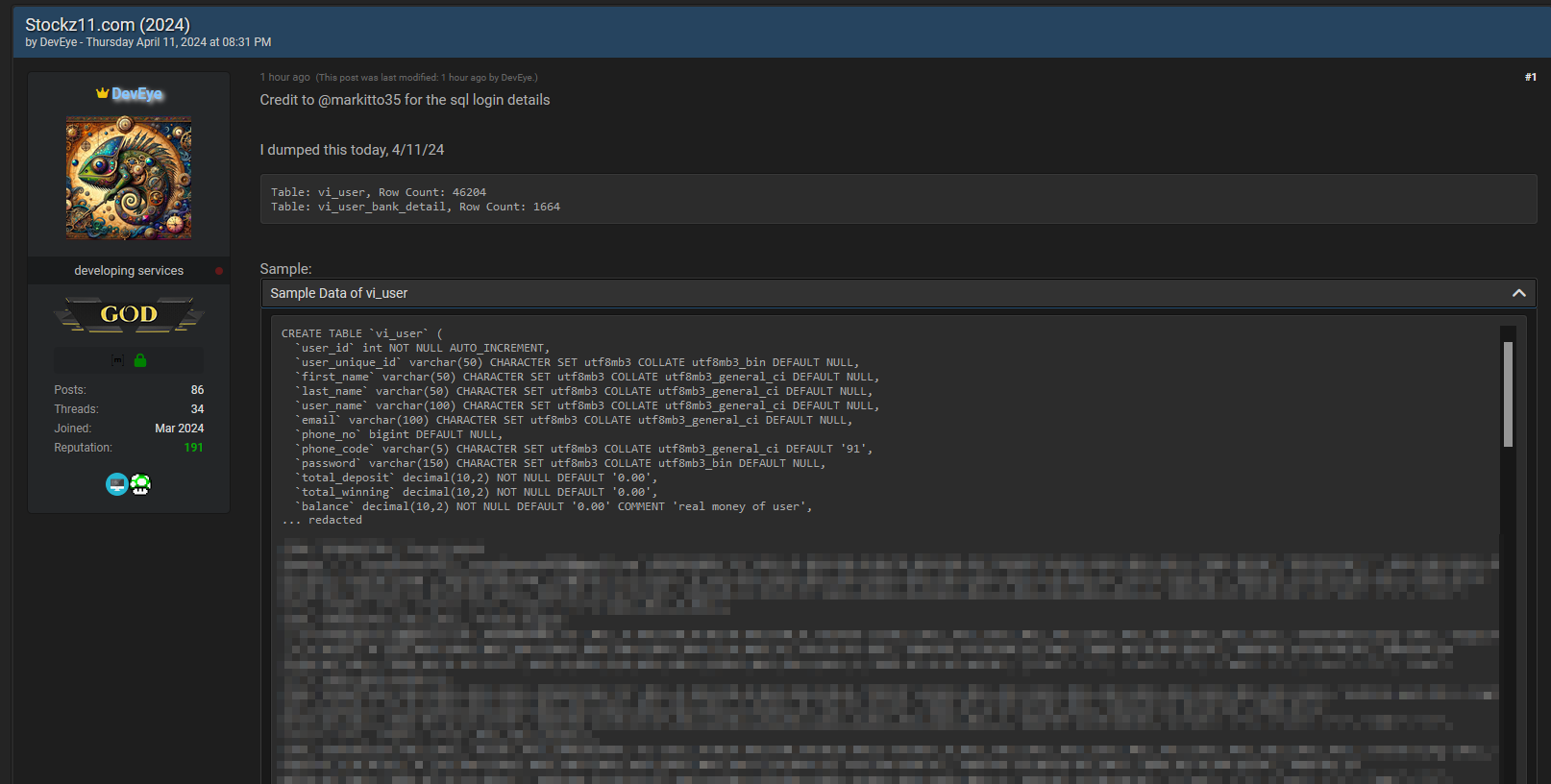
On April 11, 2024, a post surfaced on a forum from a user named DevEye, claiming to have executed a data dump of StockZ11.com. The post included details suggesting that two tables from the website’s database
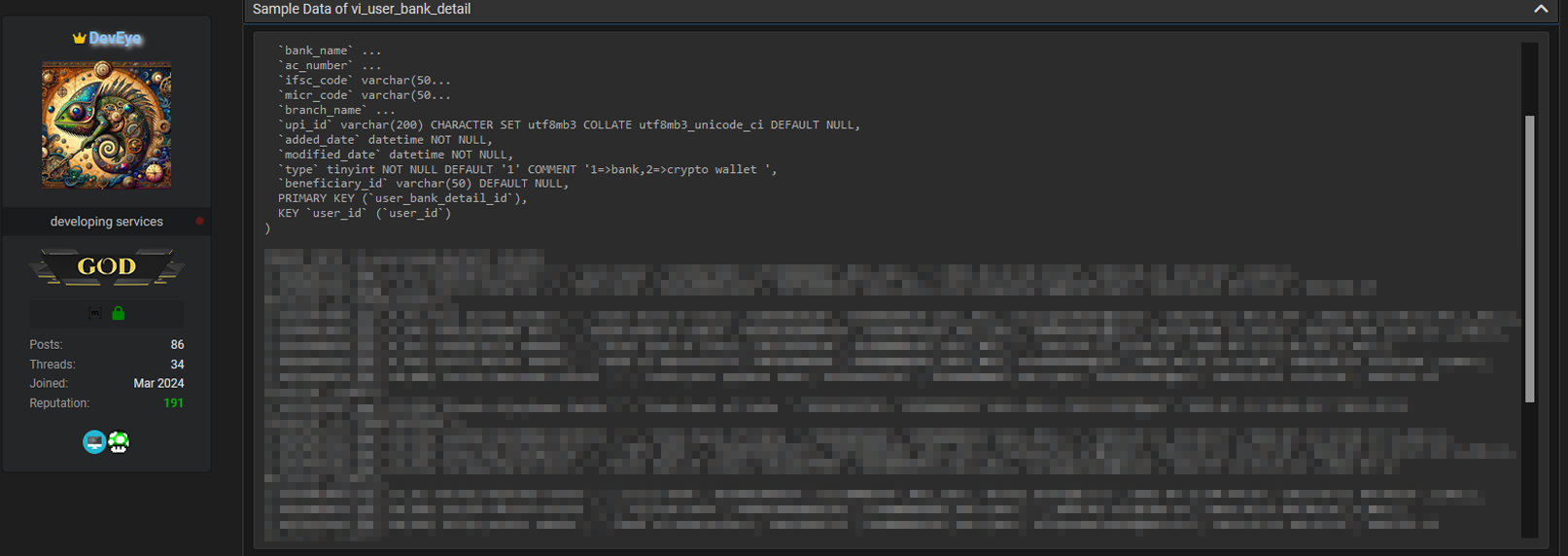
vi_userwith 462,094 entriesvi_user_bank_detailwith 1,664 entries, were compromised.
This breach could potentially expose sensitive user information, including banking details.
Threat Actor Background
The post-credits a user named markitto35 for the SQL login details, which hints at a SQL injection attack—a common vector for data breaches. SQL injection exploits vulnerabilities in a website’s database management system. DevEye, is self-described as a web developer and bug hunter, which implies a certain level of sophistication and perhaps a motive rooted in demonstrating technical prowess or disrupting the financial data market. Or perhaps they just don’t like the site. DevEye is a “GOD” level user.
“markitto35” is also mentioned in a tweet by SOCRadar:
Potential Impacts
The immediate risk involves the exposure of personal and financial information of StockZ11.com’s users. Such data can be used for identity theft, financial fraud, or sold on dark web markets. Long-term impacts may include a loss of trust in StockZ11.com, affecting their growth and user retention.
Preventive Steps for End-Users
If you’re a user of StockZ11.com, it’s crucial to take action immediately:
- Change your passwords for StockZ11.com and any other accounts using the same credentials.
- Monitor bank statements and credit reports for unusual activity.
- Be vigilant against phishing attempts that may use your personal information.
- Consider credit freeze or fraud alerts with credit bureaus.



