Sunrun Hit by Data Breach: Hacker Accesses Employee Documents
Sunrun's latest data breach exposes internal documents after hacker exploits MFA weaknesses. #CyberSecurity #DataBreach
Sunrun Inc. is a leading provider of residential solar energy systems in the United States. Headquartered in San Francisco, California, the company specializes in solar panels, energy storage solutions, and services related to home solar energy installations. Sunrun has been a significant player in the push towards renewable energy, boasting a substantial customer base and generating approximately $2.1 billion in annual revenue.
Breach Details
On August 30, 2024, a hacker operating under the alias "grep" compromised a number of employee accounts belonging to Sunrun. The attacker, who posted details of the breach on an underground forum, claimed to have accessed the accounts by exploiting a common technique known as "push notification spamming." This method is often used to bypass Multi-Factor Authentication (MFA), where the attacker bombards the target with repeated MFA push notifications until the target accidentally approves one, granting unauthorized access.
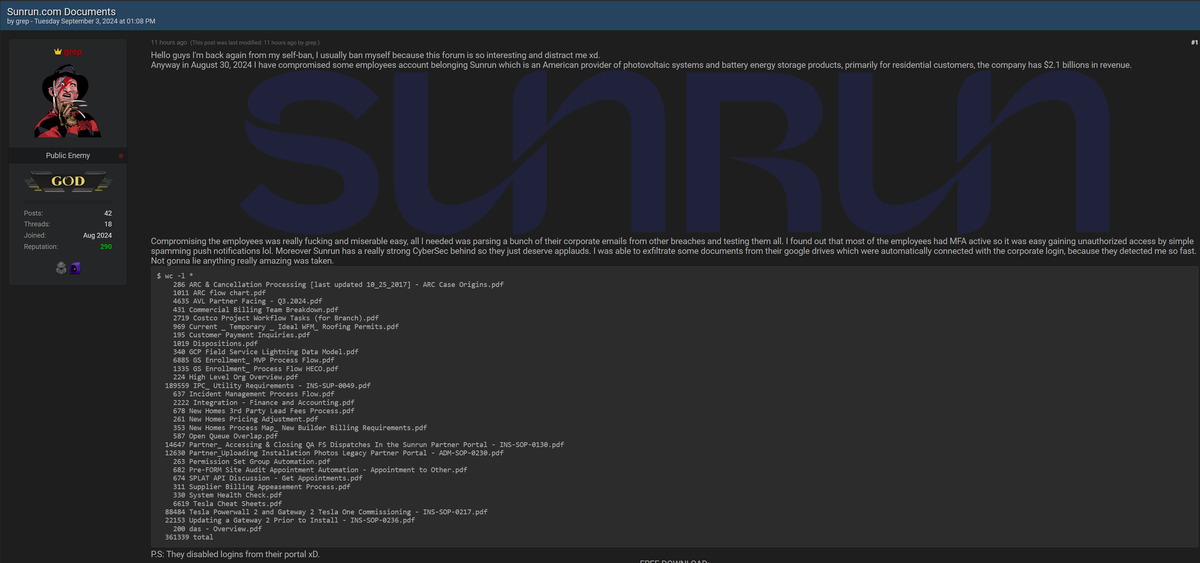
The attacker stated that although Sunrun's cybersecurity measures were generally robust, they were still able to exfiltrate several documents from employee Google Drive accounts before being detected. The files listed in the forum post include internal documents such as billing team breakdowns, customer payment inquiries, service lighting data models, and integration files related to finance and accounting. While the attacker downplayed the significance of the breach, describing the stolen documents as nothing "really amazing," the exposure of internal processes and sensitive company information poses a potential security risk to Sunrun and its stakeholders.




