Bitcoin
Understanding Illicit Bitcoin Transactions - A Detailed Analysis Using the Elliptic2 Dataset
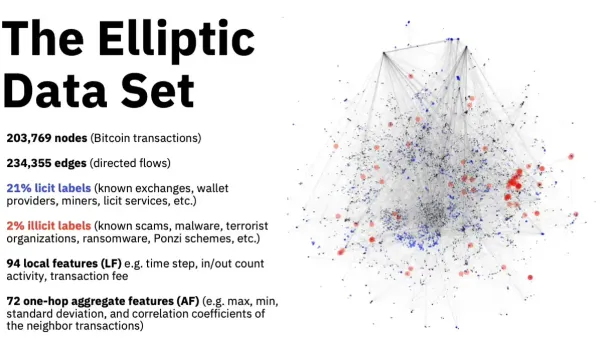
The Elliptic2 dataset, is an expansive collection of Bitcoin transaction data organized in a graph format. This dataset contains 122,000 labeled subgraphs extracted from a larger background graph consisting of 49 million nodes and 196 million transactions.
