Understanding Illicit Bitcoin Transactions - A Detailed Analysis Using the Elliptic2 Dataset
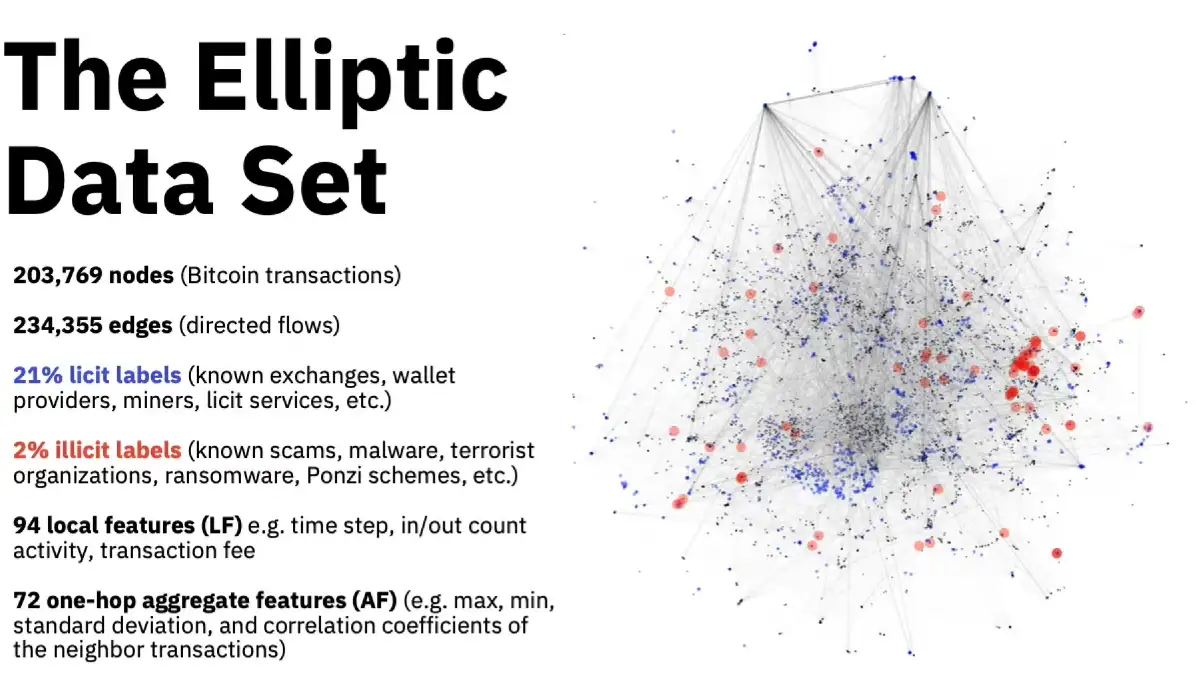
The Elliptic2 dataset, is an expansive collection of Bitcoin transaction data organized in a graph format. This dataset contains 122,000 labeled subgraphs extracted from a larger background graph consisting of 49 million nodes and 196 million transactions.
Introduction to Bitcoin and Blockchain Technology
Before getting into the analysis of illicit Bitcoin transactions, it's essential to understand the basics of Bitcoin and blockchain technology. Bitcoin is a form of digital currency, created and held electronically on a computer. Bitcoins are not printed, like dollars or euros – they’re produced by people, and increasingly businesses, running computers all around the world, using software that solves mathematical problems.
Blockchain is the technology underpinning Bitcoin. It is a public ledger of all Bitcoin transactions that have ever been executed. It is constantly growing as ‘completed’ blocks are added to it with a new set of recordings. Each block contains a cryptographic hash of the previous block, linking them in a chain. This decentralization and cryptographic linking make Bitcoin transactions secure and somewhat anonymous, but not entirely untraceable.
The Role of the Elliptic2 Dataset in Monitoring Bitcoin Transactions
The Elliptic2 dataset, developed by Elliptic in collaboration with researchers from the MIT-IBM Watson AI Lab, is an expansive collection of Bitcoin transaction data organized in a graph format. This dataset contains 122,000 labeled subgraphs extracted from a larger background graph consisting of 49 million nodes and 196 million transactions. Each node represents a transaction, and each edge represents the flow of Bitcoin between transactions, which can be visualized as a massive web of connections.
The primary goal of this dataset is to detect and analyze patterns related to financial crimes like money laundering using machine learning techniques.
How Machine Learning Techniques Uncover Illicit Activities
The application of machine learning in the context of the Elliptic2 dataset involves using algorithms to analyze the vast network of transactions to identify patterns that might suggest illegal activity. Here’s a breakdown of the three machine learning techniques used:
- GNN-Seg (Graph Neural Network Segmentation): This technique helps in understanding the relationships and flows between different nodes (transactions), identifying clusters or groups of transactions that might represent illegal activities.
- Sub2Vec: Inspired by the popular natural language processing technique word2vec, Sub2Vec is used to generate vector representations of subgraphs. These vectors help in comparing and identifying subgraphs that are similar to each other, which is crucial in spotting repeating patterns of illicit transactions.
- GLASS (Graph-based Learning for Automated Subgraph Summarization): This method focuses on summarizing large subgraphs into smaller, more manageable representations, making it easier to identify key characteristics of money laundering or other criminal activities.
Analyzing Criminal Patterns
The analysis revealed two main patterns often associated with money laundering within the Bitcoin network:
- Peeling Chains: This involves splitting a large amount of Bitcoin into smaller amounts that are gradually moved out to different addresses. It resembles peeling layers off an onion and is used to disguise the original source of funds.
- Nested Services: These are complex layers of transactions where illicit services are buried within multiple legitimate transactions, similar to Russian nesting dolls.
These patterns are significant because they help forensic analysts identify not just isolated incidents of money laundering but elaborate networks that facilitate such activities.
Implications and Future Directions
The findings from the Elliptic2 dataset have profound implications for law enforcement and financial regulators. They highlight the need for more sophisticated tools to monitor and regulate the fast-evolving landscape of cryptocurrency transactions. Future research will likely focus on refining these machine learning techniques and expanding their applicability to other cryptocurrencies beyond Bitcoin.