Unpatched Telegram for Android Vulnerability: 'EvilLoader' Exploit Discovered
EvilLoader manipulates Telegram’s file handling by taking advantage of how the application processes media files.
A newly uncovered security vulnerability in Telegram for Android, called EvilLoader, has been discovered by malware and cyber threat intelligence analyst 0x6rss. This flaw enables attackers to disguise malicious APKs as video files, allowing malware to be installed on a target's device without their knowledge. The vulnerability, which remains unpatched, affects the latest Telegram for Android version 11.7.4.
Technical Details of the EvilLoader Vulnerability
EvilLoader manipulates Telegram’s file handling by taking advantage of how the application processes media files. Attackers create an HTML file containing malicious JavaScript and rename it with an MP4 extension, making Telegram incorrectly recognize it as a video file. When a user attempts to open this file, Telegram does not play it directly but instead prompts them to select an external application to handle the media. If the user proceeds, the disguised APK file executes, resulting in the potential compromise of their device.
The core of this exploit relies on Telegram’s failure to validate file content properly, relying instead on file extensions to determine format. By embedding harmful payloads in files that appear to be harmless videos, attackers can deceive users into executing malicious code. Because Telegram is a trusted platform, many users are unlikely to suspect that opening a video file could pose a risk.
Active Exploitation in Underground Forums
This vulnerability has been actively exploited and is currently being sold on underground forums. Since January 15, 2025, the exploit has been available for purchase under the name EvilLoader, a rebranding of a previously known exploit called EvilVideo. The prior vulnerability, disclosed in July 2024 and tracked as CVE-2024-7014, operated in a nearly identical way. The first iteration of this attack allowed malicious video files to be delivered via Telegram, prompting users to install malware-laden APKs under the guise of media content.
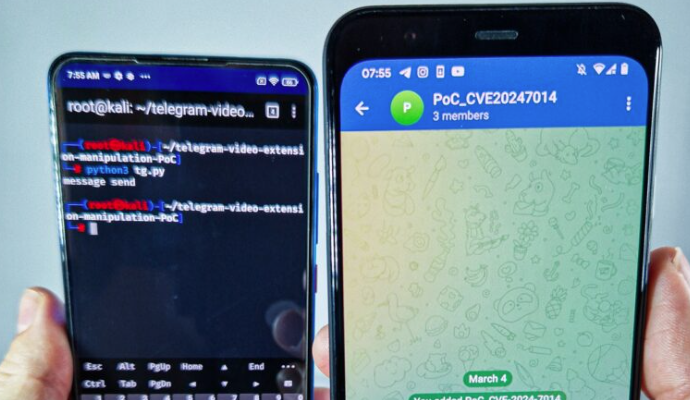
A proof-of-concept demonstration for EvilLoader has been made available by 0x6rss, showing how the exploit works in practice. The demonstration highlights that when a user receives the crafted file, Telegram’s interface makes it appear as if it is a legitimate video. If the user tries to play it, they will see a prompt asking them to open it with an external application. If they cancel the prompt, Telegram displays an error message suggesting that the video cannot be played correctly, reinforcing the illusion that it is just a corrupted file rather than an active exploit attempt. If the user instead proceeds with opening the file, the malicious APK installs and executes, leading to potential device compromise.
Security Implications and Exploit Execution
This attack is particularly dangerous because it requires minimal user interaction. While Android devices require explicit permission to install applications from unknown sources, many users unknowingly grant this permission when attempting to play the disguised video. Telegram will prompt users to install an external application, and in doing so, users will have to enable installation from unknown sources. Once this permission is granted, the malware payload executes and can perform a range of malicious activities, including data exfiltration, device control, and surveillance.
Despite being reported to Telegram on March 4, 2025, the vulnerability remains unpatched. Given that the exploit has been available for sale for nearly two months, the lack of a fix leaves users at risk. Similar past exploits, such as the EvilVideo vulnerability, were also actively sold on underground forums, indicating that cybercriminals are continuously refining and distributing such attack methods.
Mitigation Strategies
STOP USING TELEGRAM, USE SOMETHING WITH REAL SECURITY.
Mitigation strategies include being cautious when opening media files received through Telegram, particularly those requiring external applications. Telegram users should disable the auto-download feature in their settings to prevent potentially malicious files from being automatically saved to their devices. Additionally, using reputable mobile security software that detects and blocks malicious APKs can provide another layer of defense.
For those interested in further technical details, the vulnerability and proof of concept have been documented on CTI Monster in a blog post by 0x6rss. The proof-of-concept code is also available on GitHub, demonstrating how Telegram’s video extension handling can be manipulated. A previous instance of this kind of exploit was detailed in an article by WeLiveSecurity regarding the EvilVideo vulnerability. The CVE-2024-7014 entry also provides insights into how these types of flaws are cataloged and tracked.