USDoD and CVE-2024-37085
Critical VMware ESXi Vulnerability Exploited: A Deep Dive into CVE-2024-37085
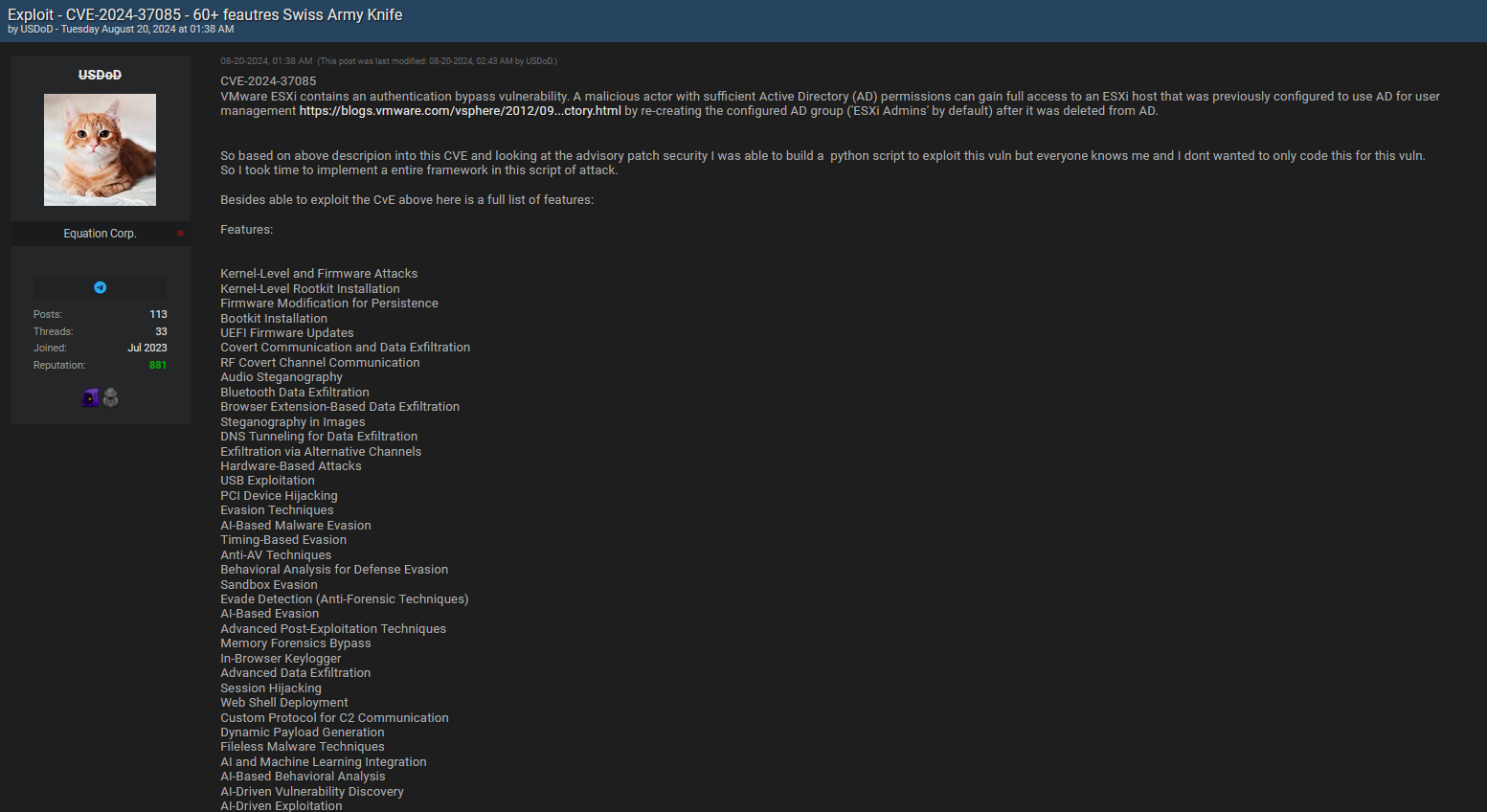
A forum post by a user named "USDoD" discusses an exploit for CVE-2024-37085, a critical vulnerability in VMware ESXi. The post reveals how this exploit can be leveraged to gain unauthorized access to ESXi hosts through an authentication bypass vulnerability, especially when Active Directory (AD) configurations are involved. The author has developed a Python script to automate the exploitation and has included a wide array of additional malicious features, transforming the tool into a versatile "Swiss Army Knife" for cyberattacks.
Excerpts
- Exploit Overview:
- "CVE-2024-37085 contains an authentication bypass vulnerability. A malicious actor with sufficient Active Directory (AD) permissions can gain full access to an ESXi host..."
- Tool Capabilities:
- "Besides being able to exploit the CVE above, here is a full list of features..."
- Features listed include:
- Kernel-Level and Firmware Attacks
- Covert Communication and Data Exfiltration
- AI-Based Malware Evasion
- In-Browser Keylogger
- Session Hijacking
- Dynamic Payload Generation
Company Overview
- VMware, Inc.
- VMware is a leading provider of cloud computing and virtualization technology. ESXi, one of its flagship products, is a hypervisor used for deploying and managing virtual machines in a data center environment.
Breach Details
- CVE-2024-37085:
- A critical vulnerability in VMware ESXi, allowing unauthorized access through an authentication bypass. This vulnerability is particularly exploitable when the ESXi host was previously configured to use Active Directory for user management.
Threat Actor Profile
- Forum User: USDoD
- Likely a skilled hacker with a deep understanding of VMware infrastructure and cybersecurity. They have created a sophisticated tool that bundles numerous attack techniques, indicating a high level of expertise.
Impact Analysis
- Potential Impact:
- Full access to ESXi hosts can lead to severe consequences, including data theft, service disruption, and the potential for broader network compromise.
- The extensive list of features makes this tool capable of more than just exploiting the mentioned CVE, posing a significant threat to organizations using vulnerable systems.




