Washington D.C. DMV and IAAI Breached: Data Compromised from 2018-2024
🚨 IAAI AuctionNow™ suffers major breach, exposing source codes & hardcoded credentials from 2018-2024! Auction systems and DMV impacted. Find out more! #CyberBreach #DataLeak #IAAI #AuctionSecurity
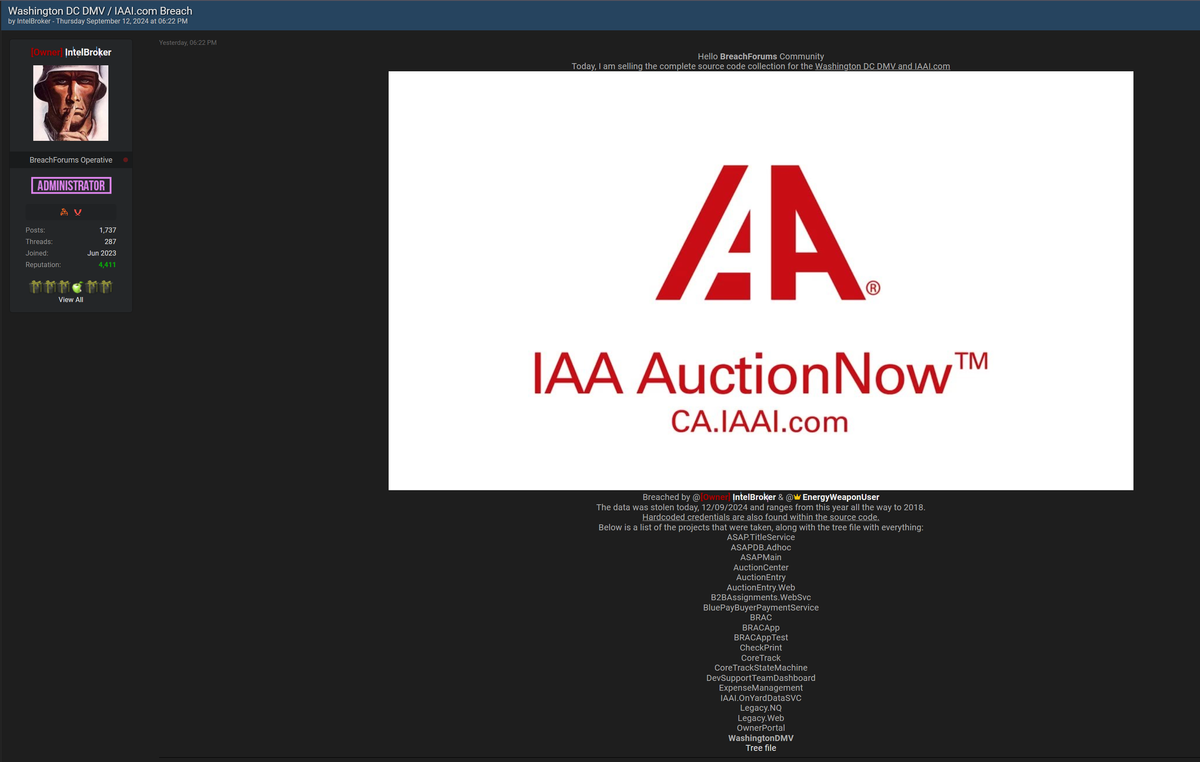
The Insurance Auto Auctions (IAA), a leading North American digital marketplace specializing in total loss, recovered, and high-mileage vehicles, finds itself in the crosshairs of a major cyber breach. IAA AuctionNow™, a part of the broader IAAI.com ecosystem, is responsible for handling critical auction services. However, recent events have shaken the company’s cybersecurity framework.
On September 12, 2024, IntelBroker, the owner of BreachForums, alongside EnergyWeaponUser, announced that the Washington D.C. DMV and IAAI had been breached. This incident marks another addition to the growing list of cyberattacks on critical infrastructures and digital marketplaces. According to the details provided in the post, the source code collection from both the Washington D.C. DMV and IAAI was stolen, with data spanning from 2018 to 2024. What makes this breach particularly alarming is the exposure of hardcoded credentials within the leaked source code, allowing for more significant potential exploitation.
IAAI: A Brief Overview
IAAI, a subsidiary of KAR Auction Services, operates in North America and specializes in providing salvage auto auction solutions to various businesses, including insurance companies, dealerships, fleet lease companies, and charitable organizations. With its focus on damaged, high-mileage, or end-of-life vehicles, IAAI has become a key player in the automotive auction sector. Their digital platforms, such as AuctionNow™, enable real-time auctions for global buyers and sellers.
However, as the company continues its digital expansion, cybersecurity challenges have increasingly threatened the integrity of these platforms. The company holds an immense amount of data, ranging from customer information to intricate auction details, making it a lucrative target for cybercriminals.
The Breach in Detail
The breach uncovered on BreachForums is substantial. Not only were source codes and hardcoded credentials leaked, but a vast array of projects related to IAAI’s infrastructure was also exposed. This included sensitive files associated with their auction operations, buyer management systems, and legacy services.
Here’s a detailed breakdown of the systems impacted by the breach:
- ASAPTitleService
- ASAPDB Adhoc
- ASAPPlanner
- AuctionCenter
- AuctionEntry
- AuctionEntry.Web
- B2BAssignments.WebSvc
- BluePayBuyerPaymentService
- BRAC
- BRACApp
- BRACAppTest
- CheckPrint
- CoreTrack
- CoreTrackStateMachine
- DevSupportTeamsDashboard
- ExpenseManagement
- IAAIONyardDataSVC
- Legacy.NG
- Legacy.Web
- OwnerPortal
- WashingtonDMV
This extensive list reveals the scope of the breach, which affects several core functionalities of the IAAI ecosystem, including legacy systems, web portals, payment services, and auction management solutions. The presence of hardcoded credentials within the source code further exacerbates the threat, providing cybercriminals easy access to potentially exploit these services.
Prior Breaches and Context
IAAI has not been immune to cyber threats in the past. While there are no documented major breaches directly associated with IAAI prior to this incident, its parent company, KAR Auction Services, has experienced cybersecurity threats in the past. This highlights the growing risk facing online automotive auction platforms, which hold substantial amounts of personal and financial data.
As the threat landscape evolves, automotive marketplaces like IAAI are increasingly targeted for their wealth of operational and customer data. This breach on BreachForums, though unique in its targeting of the IAAI source code, is indicative of the broader pattern of attacks on digital auction platforms.
Implications and Future Concerns
The breach at IAAI and the Washington D.C. DMV could have far-reaching implications for both the company and its customers. Hardcoded credentials and source code exposure increase the risk of further exploits, potentially allowing attackers to disrupt auction processes, manipulate vehicle transactions, or access private buyer and seller information.
Moving forward, IAAI must address the exposed vulnerabilities, especially those tied to legacy systems and hardcoded credentials, to prevent additional exploitation. This breach also raises concerns over the security protocols used by auction platforms, particularly those with expansive legacy infrastructures.




